In today's ever-evolving digital landscape, robust cybersecurity is no longer an option – it's a critical necessity. Businesses of all sizes face constant cyber threats, from data breaches and malware attacks to phishing scams and ransomware. But, how your company approaches cybersecurity can reveal a lot about its overall security posture.
These numbers paint a clear picture: businesses can't afford to be complacent about cybersecurity. But the "how" of cybersecurity isn't a one-size-fits-all approach. Just like companies, cybersecurity strategies can be categorized into distinct archetypes.
What Are Cybersecurity Archetypes?
The term "archetype" refers to a universal pattern or model that reflects a common theme. In cybersecurity, an archetype represents companies' specific approach to securing their data and systems. Understanding these archetypes can help you identify which best aligns with your company's needs and identify potential areas for improvement.
- A cybersecurity archetype is a generalized model representing a common approach to managing and protecting an organization's digital assets.
- It categorizes organizations based on security priorities, resource allocation, and overall risk management strategy.
- By understanding these archetypes, businesses can gain insights into their security posture.
- Archetypes provide a framework for comparing security strategies and identifying best practices.
- Identifying the correct archetype helps tailor cybersecurity initiatives for optimal results.
- Cybersecurity archetypes serve as a roadmap for navigating the complex threat landscape.
Types of Cybersecurity Archetypes
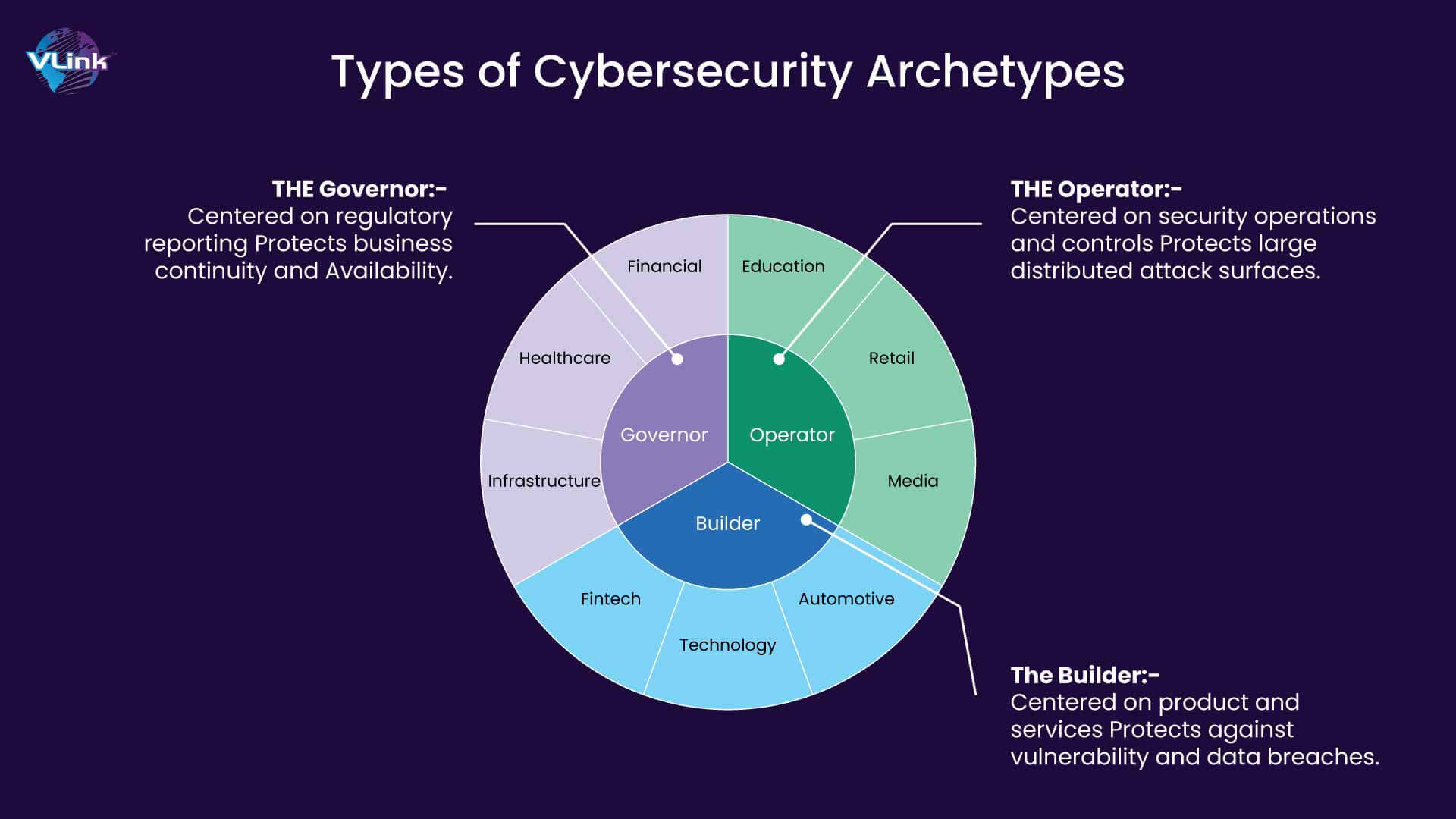
There are three primary cybersecurity archetypes, each with its strengths and weaknesses:
1. The Operator (The Pragmatist):
- Focus: Efficiency and cost-effectiveness.
- Strengths: Prioritizes quick fixes and readily adopts established security solutions.
- Weaknesses: May overlook emerging threats or need a proactive security strategy.
- Example: A small business owner who relies on essential antivirus software and regular backups.
2. The Builder (The Innovator):
- Focus: Advanced security solutions and proactive threat prevention.
- Strengths: Embraces new technologies, invests in skilled security personnel, and proactively identifies potential vulnerabilities.
- Weaknesses: Due to the focus on advanced solutions, it can be expensive and may be complex to manage for smaller companies.
- Example: A large financial institution with a dedicated security team constantly testing and implementing new security protocols.
3. The Governor (The Regulator):
- Focus: Comply with industry regulations and maintain strict controls.
- Strengths: Ensures adherence to data privacy regulations, prioritizes employee training and maintains detailed audit logs.
- Weaknesses: Can be overly restrictive, hindering innovation and employee productivity.
- Example: A healthcare provider subject to HIPAA regulations, with tight access controls and comprehensive data encryption protocols.
Which Cybersecurity Archetype Matches Your Company?
Identifying your company's cybersecurity archetype requires introspection. Here are some questions to consider:
- What is your company's cybersecurity budget?
- Do you have a dedicated security team?
- How proactive are you in identifying and patching vulnerabilities?
- How important are industry regulations in shaping your security approach?
Answering these questions will help you determine which archetype best reflects your company's security posture. There is no single "best" archetype—the most effective approach depends on your company's needs, resources, and risk tolerance.
Here’s a deeper dive into how to determine your company’s archetype:
1. Self-Assessment:
- Evaluate your organization's size and industry: These will influence the complexity of your security needs and the regulatory environment in which you operate.
- Assess your IT budget and resources: The availability of funds and personnel impacts your ability to invest in security measures.
- Examine your current security practices: Analyze your existing security controls, policies, and procedures to understand your current security posture.
- Identify your organization’s risk tolerance: Determine how much risk your company is willing to accept.
- Consider your company’s growth stage: Startups, mature businesses, and enterprises often have different security priorities.
2. Archetype Determination:
Once you've completed a thorough self-assessment, you can start to match your company's characteristics to the different cybersecurity archetypes:
- The Operator: Prioritizes efficiency and cost-effectiveness, often relying on basic security measures.
- The Builder: Invests heavily in advanced security technologies and proactive threat prevention.
- The Governor: Focuses on compliance with industry regulations and maintaining strict controls.
- The Challenged Operator: Struggles with limited resources and basic security needs.
- The Hybrid: Combines elements of multiple archetypes for a balanced approach.
Remember: There's no one-size-fits-all answer, and many organizations exhibit characteristics of multiple archetypes. The goal is to identify your primary focus and tailor your security strategy accordingly.
By accurately determining your company's cybersecurity archetype, you can develop a targeted approach to managing and protecting your digital assets.
5 Company Archetypes with Cybersecurity Considerations
Understanding the unique cybersecurity challenges different types of companies face is essential for developing effective security strategies. We can identify common security patterns by categorizing organizations into archetypes and developing tailored recommendations.
The following table outlines five common company archetypes and their associated cybersecurity considerations:
| Company Type | Security Focus | Potential Archetype | Considerations |
| Small Startup | Cost-effective and basic protection | The Operator | Prioritize user awareness training, consider managed security services. |
| Growing Mid-Sized Business | Balancing cost and security improvements | The Operator or The Builder | Invest in vulnerability assessments, consider cloud-based security solutions. |
| Large Enterprise | Comprehensive and advanced security solutions | The Builder | Build a dedicated security team, implement a layered security approach. |
| Highly Regulated Industry (Healthcare, Finance) | Strict compliance with industry regulations | The Governor | Regularly review compliance requirements, maintain comprehensive audit logs. |
| E-commerce Platform | Data security and customer trust | The Operator or The Builder | Prioritize data encryption, implement robust password policies. |
Case Studies: Real-World Examples of Cybersecurity Archetypes
Let's explore some real-world examples to visualize these archetypes in action:
Case Study 1: The Pragmatist Operator
A small retail chain with limited resources relies on free antivirus software, regular backups, and employee training to secure its data. This approach exemplifies the Operator archetype, balancing basic security measures with cost-effectiveness.
But, this company might consider vulnerability assessments to identify potential risks and explore affordable managed security services for additional protection.
Case Study 2: The Innovative Builder
A large financial institution with a robust IT department exemplifies the Builder archetype. It invests heavily in advanced security technologies, employs a dedicated cybersecurity team, and continuously monitors emerging and biggest cybersecurity threats.
This approach provides a high level of protection but comes with significant costs and complexity. It should focus on the most critical assets and streamline its security processes to optimize its efforts.
Case Study 3: The Compliant Governor
A healthcare provider strictly adheres to HIPAA regulations, conducting regular security audits and employee training. While this approach ensures compliance, it can sometimes hinder innovation and increase operational costs.
To strike a balance, they explore ways to automate compliance tasks and leverage technology to improve efficiency.
Case Study 4: The Challenged Operator
A small e-commerce startup faces limited resources but understands the importance of data security. It implements basic security measures like strong passwords and firewalls but needs more expertise to address complex threats.
To enhance its security posture, it might consider partnering with a managed security service provider or investing in cybersecurity awareness training for employees.
Case Study 5: The Hybrid Approach
Some companies successfully combine elements of different archetypes. For example, a mid-sized manufacturing company might prioritize compliance (Governor) while investing in emerging technologies (Builder) to avoid threats.
This hybrid approach can provide a well-rounded security strategy.
The Future of Cybersecurity Archetypes
Cybersecurity is constantly changing, influenced by technological advancements, evolving threat landscapes, and shifting regulatory environments. As a result, the cybersecurity archetypes we've discussed will likely grow and adapt.
One significant trend is the increasing convergence of the Builder and Governor archetypes. As regulations become more stringent and complex, even companies prioritizing innovation must adopt robust compliance frameworks. This will lead to a hybrid approach, where organizations focus on technological advancement and regulatory adherence.
Artificial intelligence (AI) and machine learning (ML) development are poised to revolutionize cybersecurity. These technologies can automate threat detection, incident response, and vulnerability assessment, enabling organizations to become more proactive in their security efforts. This could lead to a new archetype: The Predictor, which leverages AI and ML to anticipate and prevent threats.
Additionally, the growing adoption of cloud computing and the Internet of Things (IoT) services will introduce new challenges and opportunities. Cloud-based security solutions offer scalability and flexibility but require a different security mindset. With their inherent vulnerabilities, IoT devices demand a comprehensive approach to securing the entire ecosystem.
As cybersecurity becomes increasingly complex, there will be a growing need for specialized expertise. This could lead to the emergence of The Specialist archetype, focusing on niche areas like industrial control systems, cloud security, or application security.
The future of cybersecurity archetypes will likely be characterized by greater complexity, specialization, and the integration of emerging technologies. Organizations must be agile and adaptable to stay ahead of the evolving threat landscape.
By understanding the different archetypes and their potential evolution, businesses can make informed decisions about their cybersecurity strategies and invest in the necessary resources to protect their assets.
Choose VLink for Cybersecurity Services
With a deep understanding of the evolving threat landscape, VLink offers comprehensive cybersecurity services tailored to your organization's unique needs. Our team of certified experts provides proactive protection, advanced threat detection, and rapid incident response.
Why Choose VLink?
- Customized Solutions: We work closely with you to develop a cybersecurity strategy aligned with your business objectives and risk tolerance.
- Proactive Protection: Our advanced threat intelligence and prevention measures safeguard your systems from emerging threats.
- Expert Team: Our certified cybersecurity professionals bring in-depth knowledge and experience to protect your organization.
- 24/7 Support: Our dedicated support team is available around the clock to address your security concerns.
- Compliance Assurance: We help you meet industry regulations and standards, ensuring data privacy and protection.
Don't let cyber threats compromise your business—partner with VLink to build a resilient cybersecurity posture. Contact us today!
Wrap Up!
That’s it from our side in this blog. By understanding your company's cybersecurity archetype, you can take the first step toward building a robust and effective security program. By identifying your company's strengths and weaknesses, you can tailor your security strategy to address specific needs and mitigate risks.
Remember, there's no one-size-fits-all approach to cybersecurity. The key is to find the right balance between protection, cost-effectiveness, and business operations.










 Shivisha Patel
Shivisha Patel

















