The Internet of Things (IoT) has emerged as the new standard. You couldn't unplug from it if you tried, because everything from your smartphone to your automobile is a part of it.
These technological advancements have revolutionized (and continue to affect) our homes, workplaces, transportation networks, and even our relationships, influencing how we interact and communicate with others.
But like with any progress, there are hazards. Cybercriminals are growing increasingly sophisticated in their use of technology against us. IoT is still far from flawless, leaving it vulnerable to security threats.
Cybersecurity is one of the most essential aspects in the age of the Internet of Things. Here are some of the hazards connected with it, as well as some strategies to reduce those risks from the start. Understanding these can assist you in avoiding some of the most typical cybersecurity blunders and remaining secure.
Dominating age of IoT
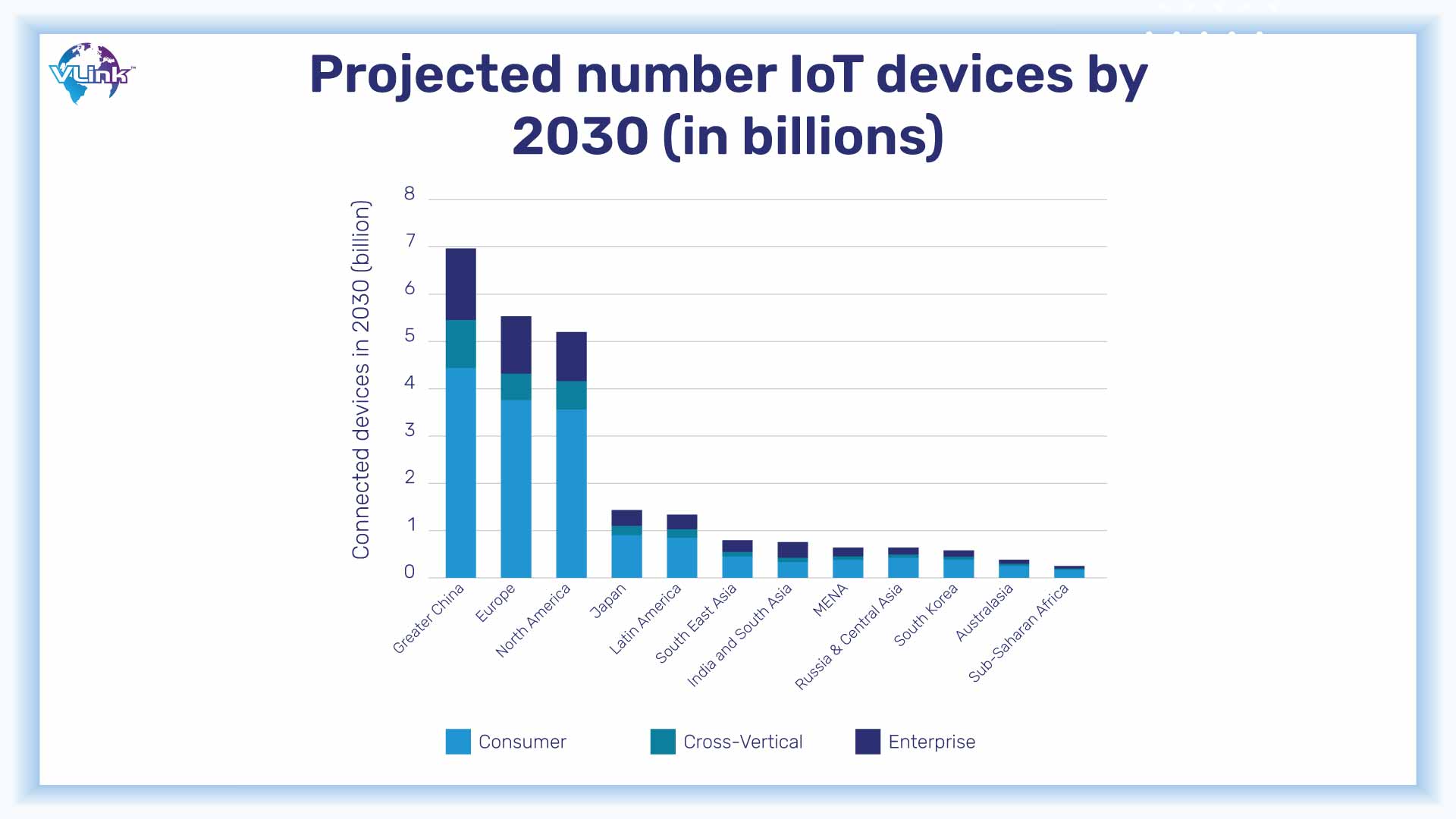
Given that there will be more than 30 billion internet-connected devices by 2020, cybersecurity might be considered the focal point of the IoT era. So many of the systems around us are linked to the Internet, from physical security to temperature management. They are handled by sophisticated networks that include both IT and OT components.
The smart building has its own Internet of Things (IoT) systems that link numerous equipment ranging from teleconference systems to personal gadgets. Multiple protocols are applied to a device once it enters the network. The protocol specifies the device's role in the larger scheme.
Many message and communication standards are in place to ensure good networking. Even with the integration of IoT in mobile app development, the level of security of these protocols is extremely important. Hackers can exploit a protocol as an access point to penetrate a network and cause damage.
Visibility can rescue the day in such situations. Monitoring a network, i.e., routine inspections of the devices and linked devices, is critical. The dangers may be promptly identified as an anomaly, tracked back to the device, and removed from the system.
Visibility and network monitoring are the initial stages in developing a cybersecurity strategy based on facts and experience. A knowledgeable cybersecurity specialist can act as a barrier between you and the world of danger.
Potential risks with IoT in cybersecurity
Understanding the hazards can assist providers and consumers in remaining secure online. Neglecting hazards may leave you vulnerable to cyberattacks, so understanding what you're up against is the first step in implementing protective measures.
Malware is harmful software that is meant to obtain unauthorized access to networks. Once access is gained, the virus may go wild and create havoc: it can steal data, drain money, slow down the system, or even cause it to collapse totally.
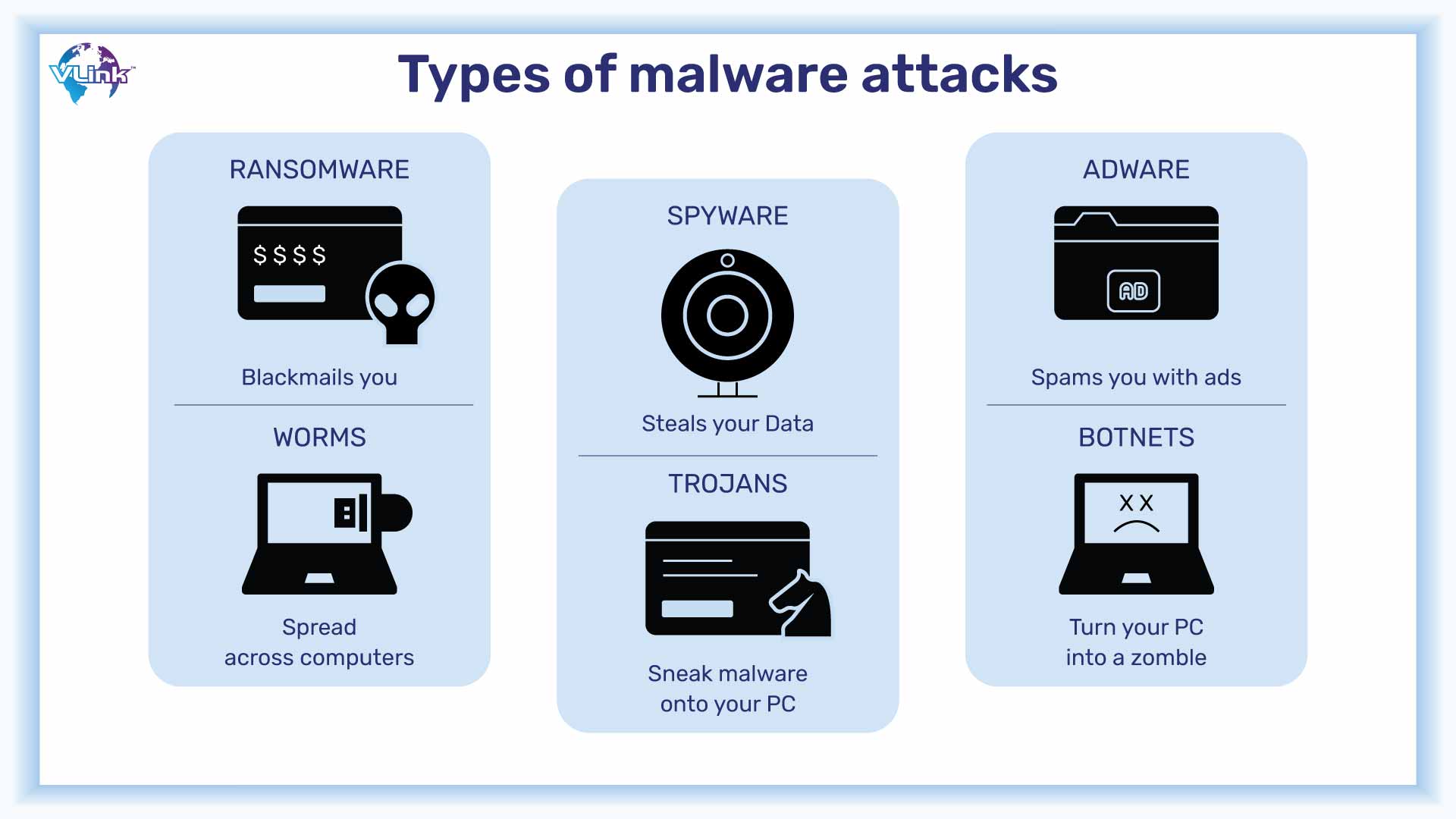
It takes numerous forms. Viruses, Trojan horses, spyware, rootkits, adware, and worms are just a few examples, which is why it's critical to constantly adapt security to detect and eliminate these types of threats.
While malware is a more passive assault, hacking is a far more aggressive approach for thieves to target networks. Almost every IoT device may be compromised, and hackers are growing more sophisticated by the day.
When a hacker has illegal access to a gadget, they can do whatever they want with it. Most hackers want to steal sensitive information, especially information that will allow them to extort money.
DDoS assaults are a type of "hacking" as well. DDoS assaults differ from traditional hacking tactics in that, rather than attempting to obtain access to a system or network, they seek to overwhelm the system with traffic to the point where it fails and may be held hostage.
Encryption is not standard on all devices. Without encryption, IoT devices are more vulnerable to hacking, making sensitive data more accessible to outsiders.
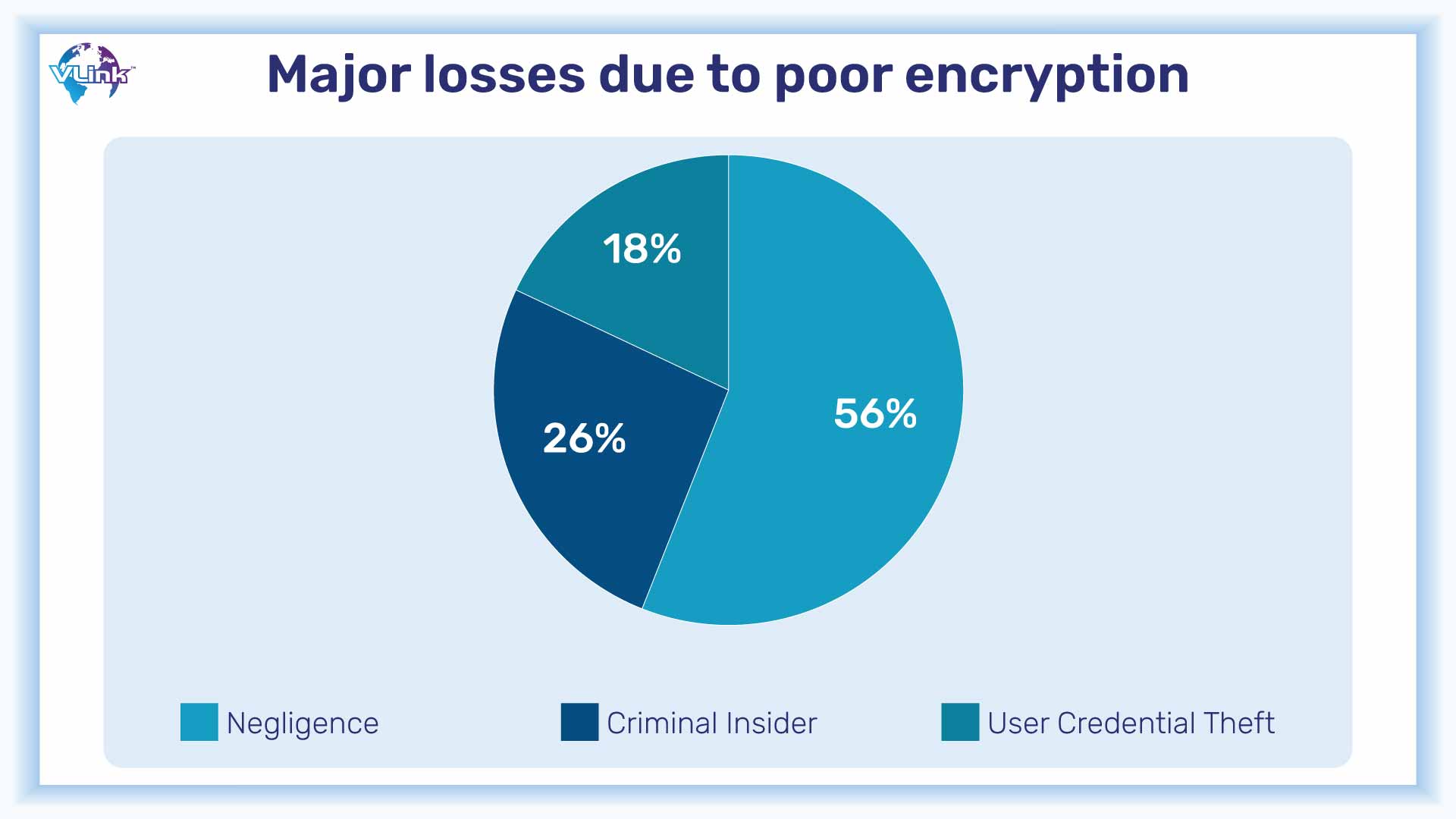
The use of encryption can be seen in different gadgets, mobile app security, websites’ privacy policies, and other digital assets, although it is still a developing technology. One should not just assume that the information received and sent by their device is encrypted.
In corporate discussions, sensitive information is frequently discussed. Email, messaging platforms like Slack, or a quick WhatsApp to your employer are all examples of insecure communication methods.
One of the most difficult issues in IoT is the absence of consistent quality standards. It's difficult to standardize security features when there are so many distinct devices, protocols, and networks. This necessitates ongoing analysis and development of new security measures, but it also means that there is always a loophole for hackers to exploit.
Also read: How to maintain data security & privacy in insurance app development?
Practices to implement and boost cybersecurity in IoT
Data shared through different connected devices and IoT applications needs to be secured with the appropriate methods. As a result, organizations must prioritize adopting a proactive strategy and installing robust IoT cybersecurity solutions to protect IoT connections and stay safe from cyber-attacks.
Here are some recommended practices for firms to follow when it comes to securing IoT connections:
The first step in password security is to create strong, one-of-a-kind passwords. Employees are frequently given generic passwords at onboarding, but they should be urged to change them as soon as feasible.
Then there's two-factor authentication. This effectively prevents non-account holders from gaining access to anything.
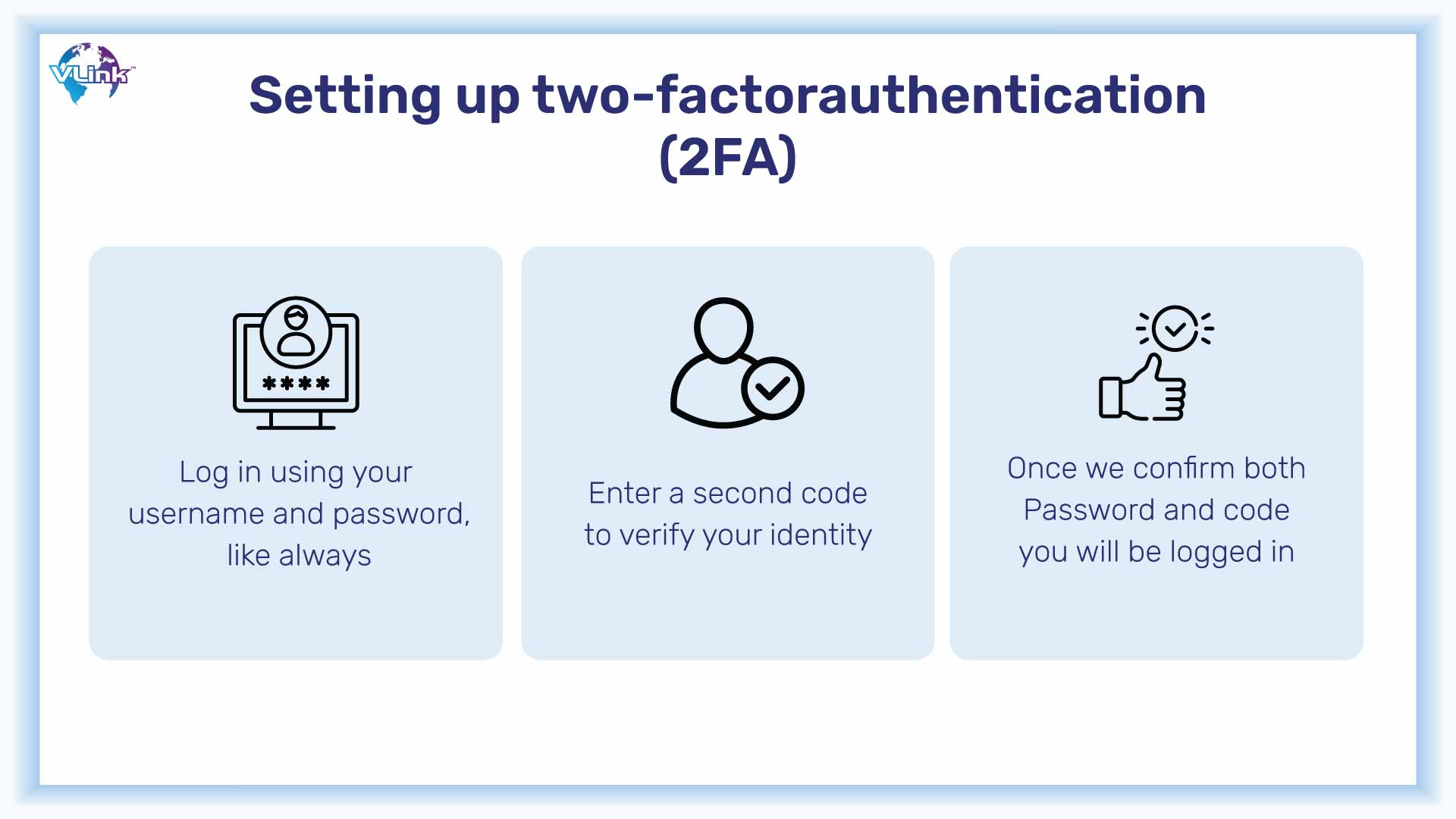
It's also a good idea to educate the account holder on the importance of not authorizing anything they haven't initiated unless it's been discussed with another party, and they know who's asking for access.
To prevent sensitive data from being accessed, every device that has the potential to contain sensitive information—which is pretty much all of them—should utilize encryption. You can't afford to be without this extra layer of security—it might be what deters hackers.
Communication is an essential component of every organization. Aside from establishing a standard communication technique inside the company or department—for example, email only, no WhatsApp conversations—the communication platform of choice should be safe.
Transport Layer Security (TLS) might be used to prevent data from being intercepted, stolen, or tampered with. To build Transport Layer Security—TLS—use a certificate-based authentication method.
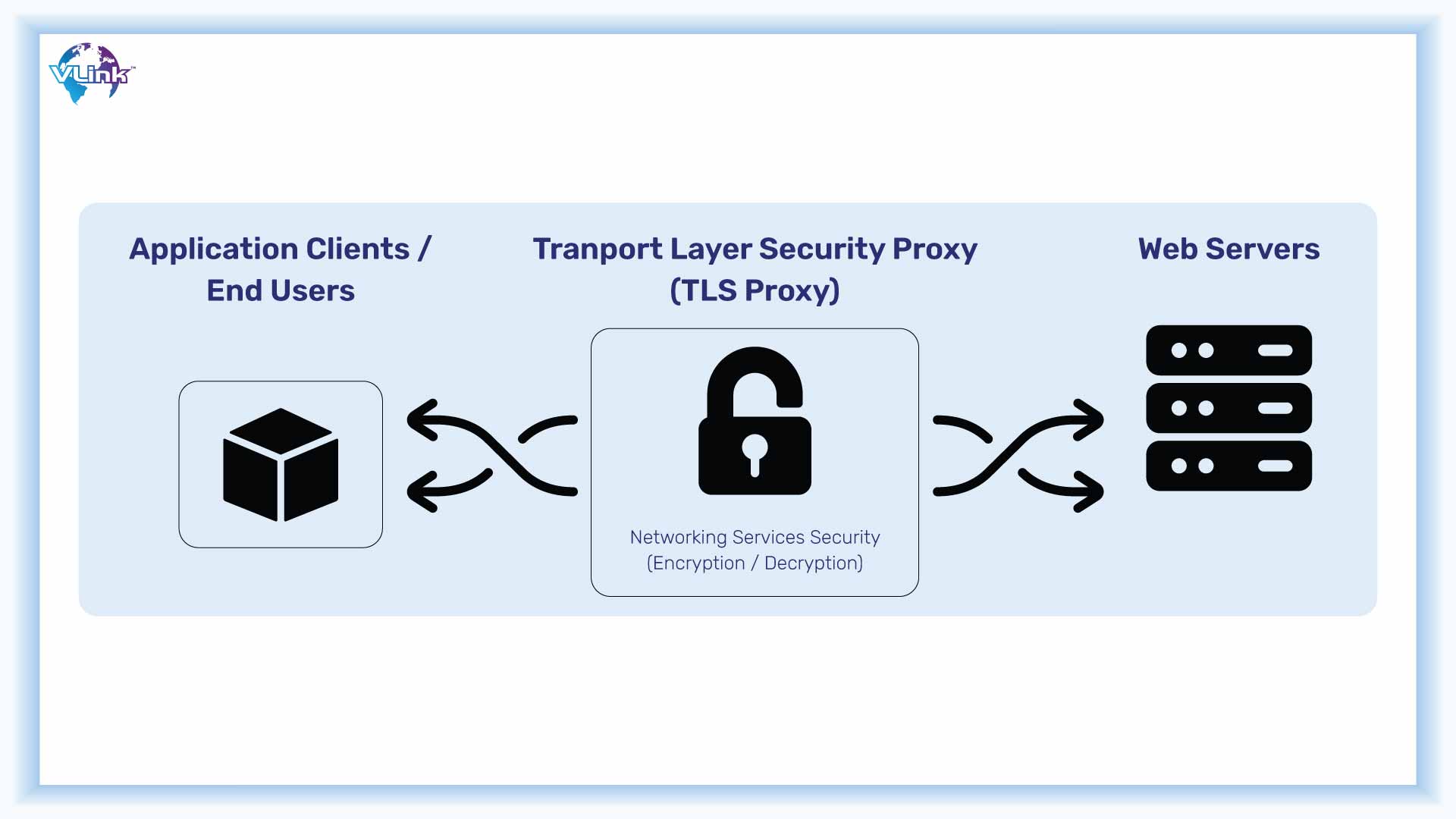
As hackers become more sophisticated, so does security. However, it does not update on its own. To ensure your security, you must keep all your systems, networks, and software up to date. Updates include new fixes for known vulnerabilities, changes to security features and protocols, and new layers for increased protection against outside influences.
Security audits is a very useful task that needs to be included possibly. It takes some work, but undertaking regular security audits may help you stay ahead of potential problems and identify potential threats before they become hazards. Regularly assessing your security also aids in the detection of trends.
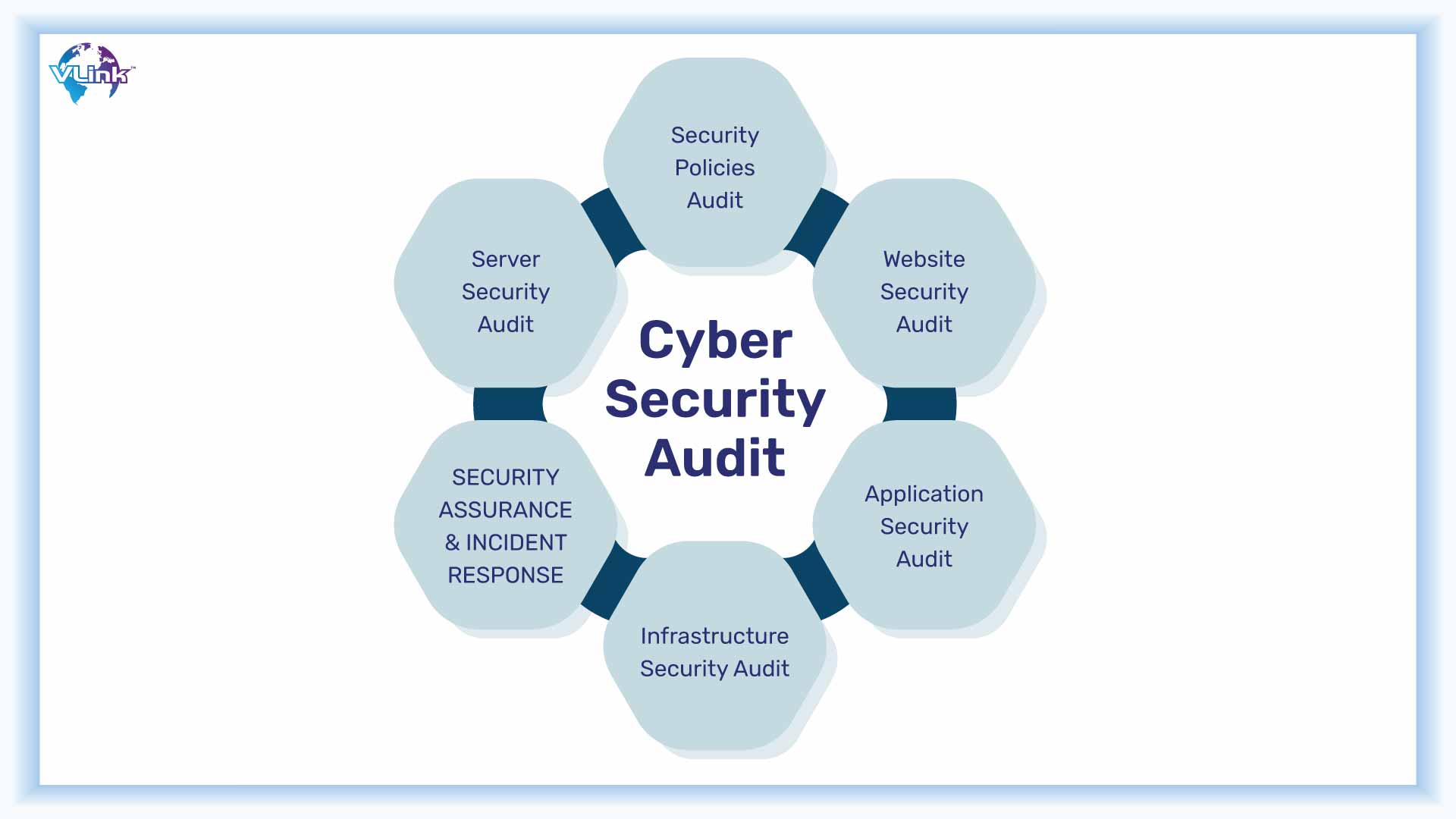
If the same threat or problem continues reappearing, it might be an indication that hackers have discovered and are exploiting a vulnerability. This means you must move quickly to repair it before it splits and lets water in.
Conclusion
It's critical to realize that on the Internet of Things era, everything is connected to everything else. This implies you must be particularly cautious when it comes to cybersecurity – everything from your SMS messages to your website hosting.
Whatever your industry, you can't avoid the Internet of Things. Risks become your risks, and solutions become your solutions as well. Not only do large firms like Microsoft have to be concerned about these issues. Even a small breach of network can harm tons of data and will take unexpected costs to repair the losses.
Reinforce Cybersecurity in IoT with VLink
As IoT devices become more prevalent and the danger of possible assaults increases, the demand for more inventive solutions to protect systems from potential cyberattacks develops. To monitor, manage, and avoid these security problems, organizations must take proactive efforts.
Collaboration with a reputable and competent IoT app development company, such as VLink, may be quite advantageous in this attempt. We provide a complete set of solutions that are suited to the unique requirements of enterprises working in the IoT landscape.
Our effective team of software developers and cybersecurity experts have fundamental competencies in safe software development, threat intelligence, and incident response, assisting organizations in reinforcing their IoT ecosystems and ensuring a solid cybersecurity infrastructure.
Businesses may dramatically improve their IoT cybersecurity while securing key assets and keeping consumer confidence in this linked world by employing our IoT development services.
Even if you haven't been the victim of a hack, you should prioritize cybersecurity today. You'll be glad you did when that first incidence occurs and no damage results.








 Shivisha Patel
Shivisha Patel

















