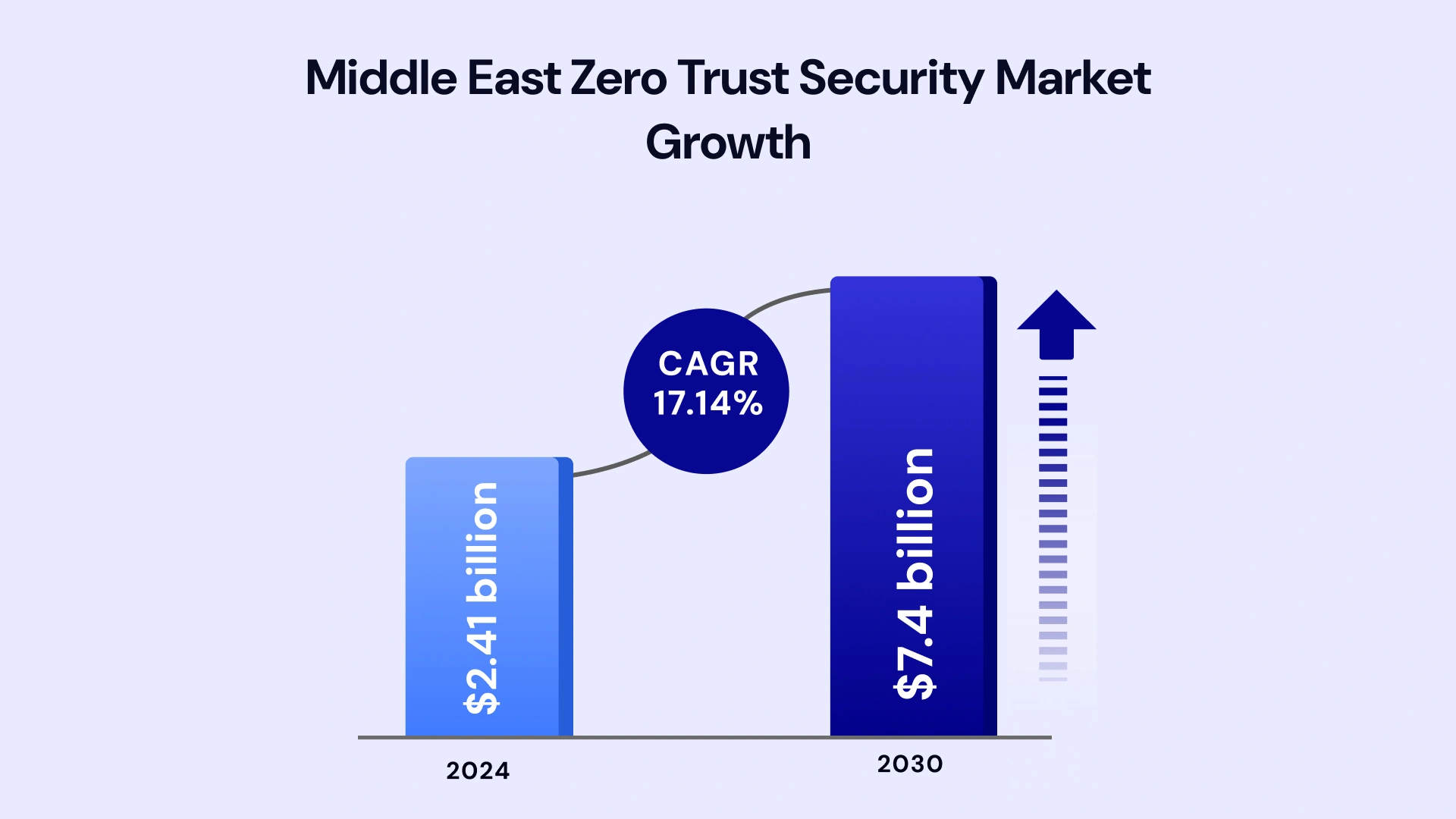
The Middle East cybersecurity market is projected to reach USD 40.97 billion by 2030, growing at a CAGR of 14.80%. Within this landscape, GCC enterprises face a stark reality: legacy perimeter security models are crumbling under the weight of sophisticated identity-led attacks, third-party vulnerabilities, and rapid cloud adoption.
Organizations across the region are increasingly turning to comprehensive cybersecurity services to address these challenges while maintaining compliance with stringent regional regulations. The convergence of digital transformation initiatives, cloud migration programs, and evolving threat actors creates unprecedented pressure on security architectures designed for a different era.
This playbook provides a GCC-specific roadmap for implementing zero trust security architecture, addressing the unique compliance requirements, hybrid cloud challenges, and operational realities facing enterprises in the UAE, Saudi Arabia, and the broader Gulf region.
Why Perimeter Security Is Failing GCC Enterprises
Traditional castle-and-moat security models were built for an era when enterprise assets resided within well-defined network boundaries. Today, GCC enterprises operate in fundamentally different environments where the perimeter has effectively dissolved.
The GCC Threat Landscape: Identity-Led Attacks & Third-Party Risk
The region has witnessed critical infrastructure breaches that exposed vulnerabilities in perimeter-centric approaches. Identity-based attacks now represent the primary threat vector, with attackers targeting compromised credentials, privileged accounts, and third-party access points rather than attempting to breach firewalls directly.
Consider the operational reality of a Saudi BFSI institution or UAE government entity managing contractor access across multiple cloud environments. A single compromised vendor credential can bypass years of perimeter investments, granting attackers lateral movement across critical systems. This is not a hypothetical scenario. Regional organizations have experienced significant exposure through vendor and contractor access pathways that traditional security models failed to address.
The challenge intensifies when enterprises onboard external partners for digital transformation initiatives aligned with Saudi Vision 2030 or UAE's national digitization programs. Each third-party connection introduces potential breach pathways that perimeter defenses cannot adequately monitor or control. As organizations embrace artificial intelligence in digital transformation, the attack surface expands exponentially, creating new vectors that traditional security cannot address.
Regional threat intelligence indicates that GCC organizations face targeted attacks from sophisticated threat actors who understand the economic significance of the Gulf's energy, financial, and government sectors. These adversaries conduct extensive reconnaissance, identify privileged accounts, and exploit trust relationships between organizations and their vendors. The increasing adoption of machine learning development services and AI-powered tools by attackers further complicates defense strategies.
Why VPNs and Castle-and-Moat Models Break in Hybrid Cloud Environments
VPN-based remote access solutions struggle to scale with modern enterprise requirements. When nearly 70% of regional companies are planning cloud migration, the limitations of legacy network access become acute. VPNs authenticate users at the perimeter and then grant broad network access, creating exactly the conditions that attackers exploit for lateral movement.
In hybrid and multi-cloud environments spanning AWS, Azure, and on-premises infrastructure, the traditional perimeter becomes meaningless. Data flows between cloud providers, employees access applications from personal devices, and workloads shift dynamically based on demand. Attempting to secure this environment with perimeter-focused tools creates visibility gaps, compliance risks, and operational friction that impedes business agility.
Enterprise leaders investing in cloud infrastructure development services recognize that cloud-native architectures require fundamentally different security approaches. The shared responsibility model shifts security obligations in ways that perimeter-focused strategies cannot accommodate. When data resides across multiple jurisdictions and cloud providers, organizations need security controls that travel with workloads rather than defending fixed network boundaries.
The operational overhead of maintaining VPN infrastructure at enterprise scale presents additional challenges. Capacity constraints during peak usage, complex troubleshooting requirements, and inconsistent user experiences drive shadow IT adoption that further undermines security posture. Modern enterprises need security solutions that enhance rather than impede productivity.
What Is Zero-Trust Security Architecture? (Beyond the Buzzwords)
Zero trust security architecture represents a fundamental paradigm shift in how enterprises approach cybersecurity. Rather than assuming trust based on network location, zero trust operates on the principle that threats exist both inside and outside the network, requiring continuous verification of every access request.
"Never Trust, Always Verify" Explained for Enterprise Leaders
The zero-trust framework eliminates implicit trust. Every user, device, and application must authenticate and authorize before accessing any resource, regardless of whether the request originates from inside the corporate network or from a remote location. This applies equally to the CEO accessing financial reports and the HVAC system connecting to building management software.
For GCC enterprise leaders, this means implementing identity-centric security controls that verify not just who is requesting access, but also the health of their device, the sensitivity of the data being accessed, the context of the request, and the behavioral patterns that might indicate compromise. Continuous authentication replaces the single sign-on model where one successful login grants persistent access.
The philosophical shift extends beyond technology to encompass organizational culture and operational processes. Security teams must move from defending perimeters to managing risk across every access decision. This requires investment in AI development services that enable real-time analysis of access patterns and automated response to anomalous behavior.
Zero Trust vs Traditional Security Models (CXO Comparison)
| Aspect | Traditional Perimeter Security | Zero Trust Security Architecture |
| Trust Model | Trust internal network, verify external | Never trust, always verify all requests |
| Access Control | Network location-based | Identity, device, and context-based |
| Verification | One-time at perimeter | Continuous throughout session |
| Lateral Movement | Possible after initial access | Restricted through micro-segmentation |
| Visibility | Limited once inside network | Complete across all users and devices |
| Cloud Compatibility | Requires complex configurations | Cloud-native and hybrid-ready |
| Compliance Alignment | Manual evidence collection | Automated policy enforcement and logging |
| Scalability | Hardware-dependent expansion | Software-defined, elastic scaling |
| Third-Party Access | Complex VPN configurations | Application-specific controlled access |
| Incident Response | Broad network forensics required | Granular access logs enable rapid investigation |
Zero Trust Security Model vs Zero Trust Network Access (ZTNA)
Understanding the distinction between zero trust as a framework and ZTNA as a specific technology matters for implementation planning. The zero trust security model encompasses the complete strategic approach covering identity, devices, networks, applications, and data. It guides organizational security posture across all domains.
ZTNA represents one component within this broader framework, specifically addressing secure application access. ZTNA solutions replace VPNs by providing application-level access rather than network-level access, ensuring users connect only to authorized applications without gaining broader network visibility. While ZTNA is essential for zero trust implementation, it alone does not constitute a complete zero trust architecture.
Organizations evaluating ZTNA solutions should assess integration capabilities with existing identity providers, support for legacy applications, and alignment with compliance requirements specific to GCC jurisdictions. The transition from VPN to ZTNA represents a significant architectural change that requires careful planning and phased deployment.
Core Pillars of a Zero-Trust Security Architecture
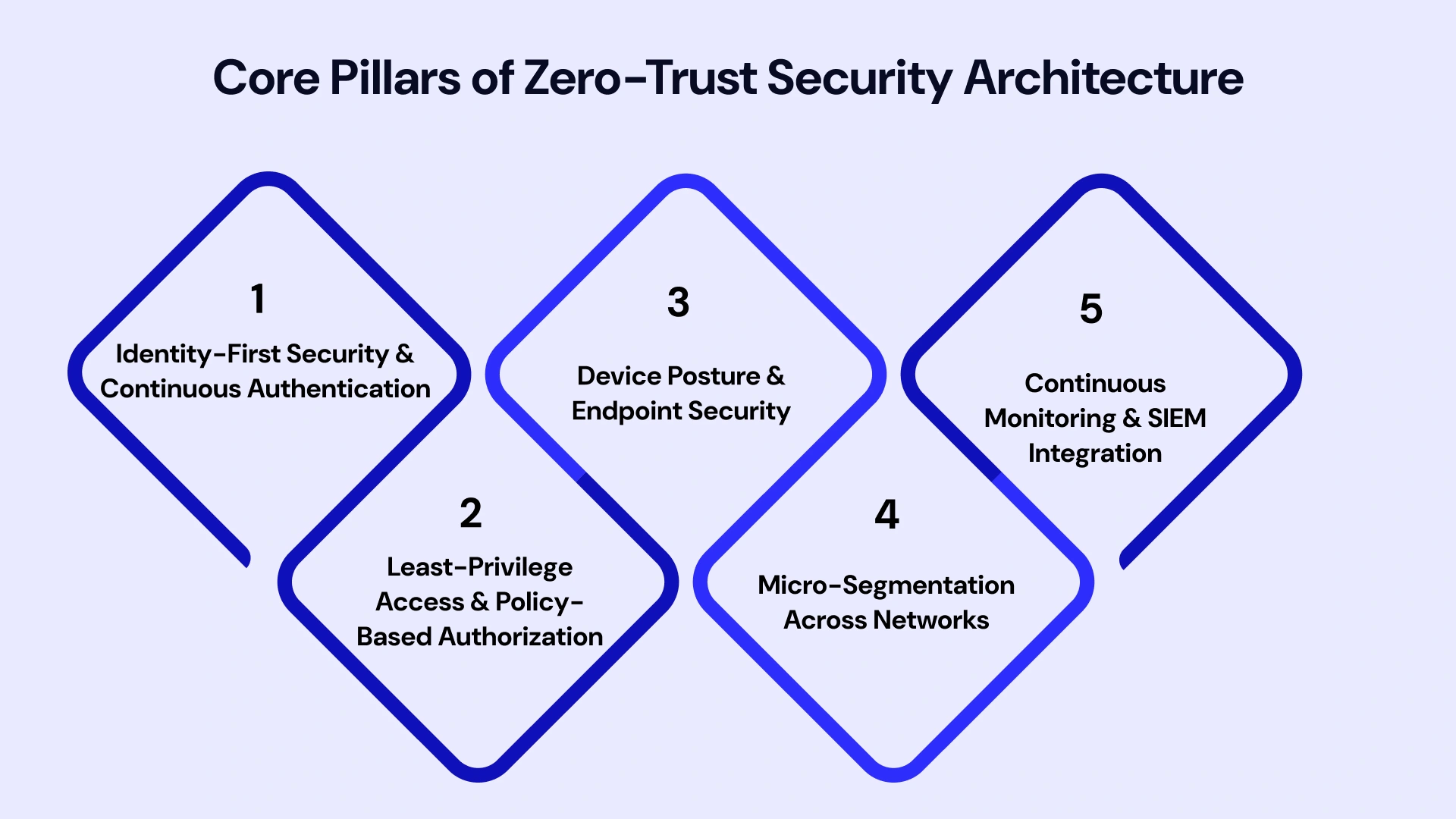
Identity-First Security & Continuous Authentication
Identity serves as the foundation of zero trust. Every access decision begins with verifying who is requesting access and whether their identity claims are legitimate. This extends beyond simple username-password combinations to encompass multi-factor authentication, behavioral analytics, and risk-based authentication that adjusts requirements based on context.
For GCC enterprises, implementing identity-first security means deploying robust IAM platforms that integrate with existing directory services while supporting modern authentication standards. Organizations often begin their zero trust journey by consolidating identity infrastructure and establishing centralized policy enforcement points.
Continuous authentication monitors user behavior throughout sessions, detecting anomalies that might indicate account compromise. If a user typically accesses financial systems during business hours from a UAE IP address, a sudden 3 AM access attempt from an unfamiliar location triggers additional verification requirements or automatic session termination.
Modern identity platforms leverage conversational AI development capabilities to provide intelligent authentication experiences. Voice biometrics, behavioral analysis, and contextual verification create frictionless experiences for legitimate users while presenting significant obstacles for attackers attempting to use stolen credentials.
Least-Privilege Access & Policy-Based Authorization
The principle of least privilege ensures users receive only the minimum access required for their specific job functions. Zero trust architecture best practices dictate that access permissions should be granular, time-limited, and regularly reviewed. Standing privileges that persist indefinitely represent security debt that accumulates over time.
Policy-based authorization automates access decisions based on predefined rules incorporating user attributes, device posture, resource sensitivity, and environmental factors. When a contractor requests access to project documentation, the policy engine evaluates their role, project assignment, device compliance status, and current threat intelligence before granting or denying access.
Just-in-time access provisioning reduces the window of opportunity for attackers exploiting compromised accounts. Rather than maintaining permanent elevated privileges, administrators request temporary access for specific tasks. Automated workflows approve or deny requests based on justification, risk assessment, and compliance requirements. This approach significantly reduces the blast radius of credential compromise.
Device Posture, Endpoint Security & Workload Trust
Zero trust extends verification beyond user identity to encompass the devices and workloads requesting access. An authenticated user on a compromised device still represents a threat vector. Device posture assessment evaluates whether endpoints meet security requirements: current patches, active endpoint protection, disk encryption, and compliance with organizational security policies.
For enterprises managing distributed workforces across GCC locations, endpoint security integration ensures that only healthy, compliant devices gain access to sensitive resources. This becomes particularly important when supporting bring-your-own-device policies or managing contractor equipment that may not meet internal security standards.
Workload trust applies similar principles to application-to-application communication. In cloud-native environments, services must authenticate to each other rather than relying on network location for trust. Service mesh technologies enable mutual TLS authentication between microservices, ensuring that only authorized workloads can communicate.
Organizations implementing DevOps consulting services benefit from integrating security controls into deployment pipelines. Infrastructure-as-code approaches enable consistent security configuration across environments while automated compliance scanning identifies misconfigurations before they reach production.
Micro-Segmentation Across Enterprise and Cloud Networks
Micro-segmentation divides networks into isolated segments, limiting lateral movement even if attackers breach initial defenses. Rather than a flat network where compromised credentials provide broad access, micro-segmented environments contain breaches within specific zones.
Implementing micro-segmentation in enterprise networks requires understanding application dependencies and communication patterns. Organizations should map traffic flows before implementing segmentation to avoid disrupting legitimate business processes. In cloud environments, security groups and network policies enable fine-grained segmentation without requiring physical network changes.
For GCC enterprises operating hybrid infrastructures, micro-segmentation must span on-premises data centers, private clouds, and public cloud deployments. Consistent policy enforcement across these environments ensures that zero trust principles apply uniformly regardless of where workloads reside. Software-defined networking technologies simplify segmentation management while providing the visibility necessary for effective security operations.
Continuous Monitoring, SIEM & SOC Integration
Zero trust architecture generates substantial telemetry that security operations teams must collect, correlate, and analyze. SIEM integration aggregates logs from identity systems, network devices, endpoints, and cloud services into a unified platform for threat detection and investigation.
SOC teams operating under zero-trust models shift from perimeter-focused monitoring to identity-centric analysis. Rather than watching for firewall breaches, analysts investigate authentication anomalies, privilege escalation attempts, and behavioral deviations that might indicate compromise. This requires updated runbooks, analyst training, and potentially AI-driven analytics to manage the increased data volume.
Organizations already utilizing SIEM platforms should evaluate how zero trust telemetry integrates with existing workflows. Leveraging data analytics services helps enterprises process zero trust security data at scale while maintaining the human oversight essential for complex incident investigation. The combination of automated detection and human analysis creates defense-in-depth that addresses both known and novel threats.
Security orchestration, automation, and response (SOAR) platforms enhance SOC efficiency by automating routine investigation and response tasks. When zero trust controls detect suspicious access patterns, automated playbooks can gather additional context, escalate to analysts, and initiate containment actions without requiring manual intervention for every alert.
Zero Trust for GCC Compliance and Regulatory Alignment
Regulatory compliance represents both a driver and a constraint for zero trust implementation in the GCC. Understanding how zero trust maps to regional frameworks simplifies compliance while strengthening security posture.
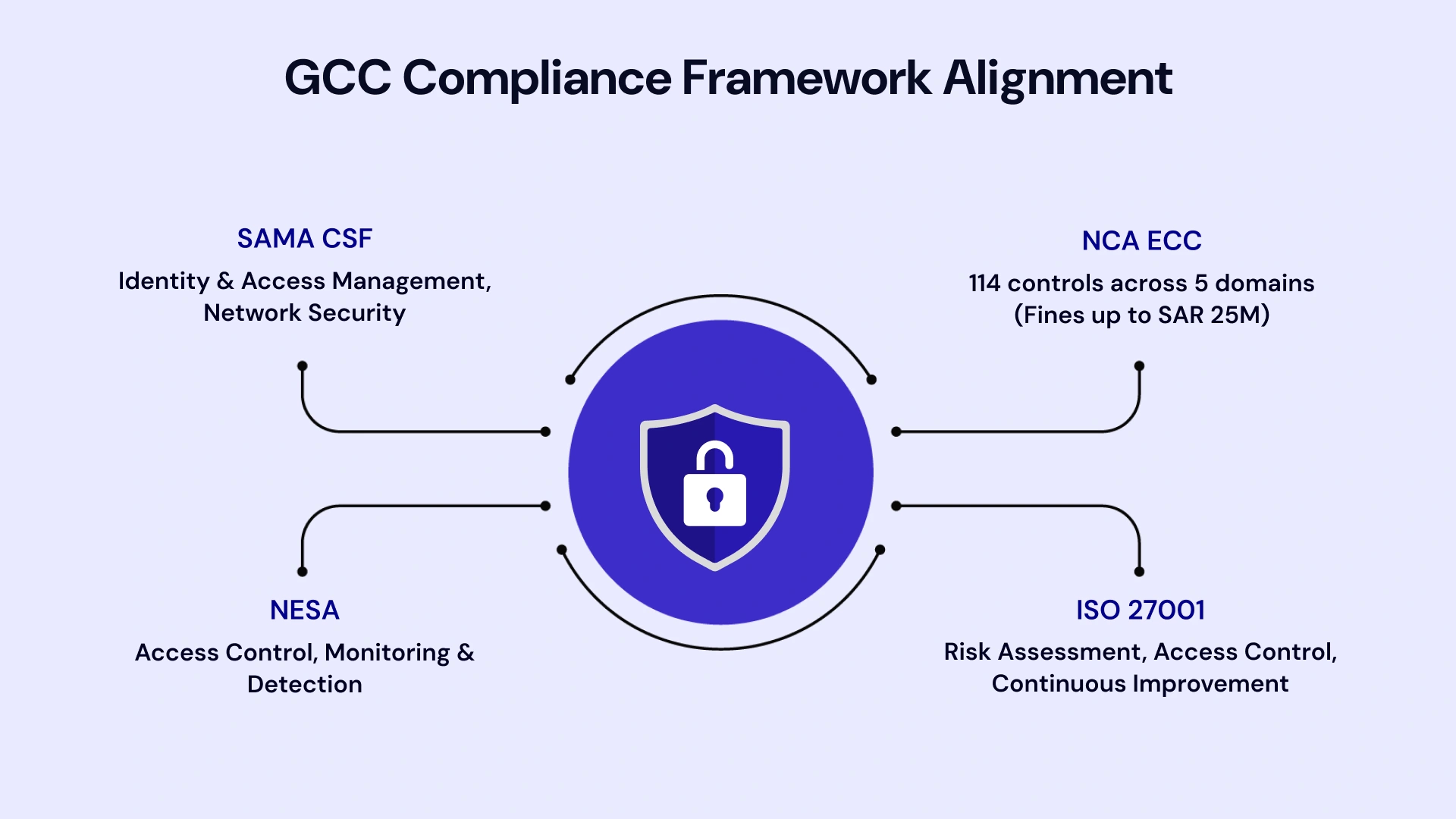
Mapping Zero Trust to SAMA, NCA, NESA & ISO 27001
The UAE's National Electronic Security Authority (NESA) standards similarly emphasize identity management, access control, and continuous monitoring. Organizations implementing zero trust architecture find that compliance evidence generation becomes automated through policy enforcement logs and access decision records.
ISO 27001 certification, increasingly required for enterprises operating in regulated GCC industries, aligns naturally with zero trust principles. The standard's emphasis on risk assessment, access control, and continuous improvement mirrors zero trust implementation methodologies. Organizations pursuing ISO 27001 certification can leverage zero trust investments to demonstrate compliance across multiple control domains.
Zero Trust Alignment with GCC Compliance Frameworks
| Zero Trust Pillar | SAMA CSF Alignment | NCA ECC Controls | NESA Standards | ISO 27001 Controls |
| Identity & Access | 3.3 Identity & Access Management | Cybersecurity Governance Domain | Access Control Requirements | A.9 Access Control |
| Least Privilege | 3.3.4 Privileged Access Management | Asset Management Controls | Authorization Standards | A.9.2 User Access Management |
| Micro-Segmentation | 3.4 Network Security | Technology Protection Domain | Network Security Controls | A.13 Communications Security |
| Continuous Monitoring | 3.6 Security Operations | Risk Management Controls | Monitoring & Detection | A.12 Operations Security |
| Device Security | 3.5 Endpoint Security | People Security Domain | Endpoint Protection | A.8 Asset Management |
| Data Protection | 3.7 Data Security | Data Governance Controls | Information Classification | A.8.2 Information Classification |
How Zero Trust Simplifies Audit Readiness in UAE & Saudi Arabia
Zero trust implementations generate comprehensive audit trails as a natural byproduct of continuous verification. Every access decision, authentication event, and policy enforcement action creates log entries that auditors can review. This automated evidence collection dramatically reduces the manual effort required for compliance audits.
Organizations preparing for SAMA assessments or NCA audits benefit from centralized policy management that demonstrates consistent control application across the enterprise. Rather than assembling evidence from disparate systems, compliance teams can generate reports directly from zero trust platforms showing policy coverage, access patterns, and security exceptions.
The continuous nature of zero trust monitoring supports the shift from point-in-time compliance assessments to continuous compliance monitoring. Real-time dashboards display compliance status across control domains, enabling proactive remediation of gaps before audits occur. This approach reduces audit preparation burden while improving actual security posture.
Data Sovereignty & Identity Governance in Multi-Cloud Setups
GCC data sovereignty requirements mandate that certain data categories remain within national borders. Zero trust architecture supports data sovereignty through policy-based controls that restrict data access and movement based on classification. When implementing multi-cloud strategies across AWS, Azure, and regional cloud providers, organizations can enforce data residency requirements through identity governance policies.
Identity governance becomes critical when managing cross-border operations. Enterprises operating across UAE, Saudi Arabia, and other GCC nations must ensure that identity data handling complies with each jurisdiction's requirements while maintaining unified access policies. Federated identity architectures enable centralized policy management while respecting data localization mandates.
Organizations investing in Microsoft business solutions benefit from integrating zero trust principles from the outset rather than retrofitting security controls after migration. Microsoft's security ecosystem, including Azure Active Directory and Microsoft Defender, provides native zero trust capabilities that align with GCC compliance requirements while supporting hybrid deployment models.
A Practical Zero-Trust Implementation Roadmap for Enterprises
Phase 1 – Zero Trust Readiness & Maturity Assessment
Before implementing zero trust controls, enterprises must understand their current security posture, existing capabilities, and organizational readiness. This assessment phase identifies gaps between current state and zero trust requirements, informs prioritization decisions, and establishes baseline metrics for measuring progress.
Zero Trust Maturity Assessment Components:
Begin by inventorying existing identity infrastructure, network architecture, and security tools. Evaluate how well current systems support zero trust principles: Can you verify identity continuously? Do you have visibility into device posture? Can you enforce granular access policies? Understanding these capabilities guides implementation planning.
Assess organizational readiness beyond technology. Zero trust implementation requires changes to how IT teams operate, how users access resources, and how security teams monitor the environment. Executive sponsorship, change management planning, and stakeholder communication are essential for success.
Conduct threat modeling specific to your organization's risk profile. GCC enterprises in different sectors face distinct threat actors with varying tactics, techniques, and procedures. Understanding the threats you face helps prioritize zero trust investments where they deliver maximum risk reduction.
Phase 2 – Identity, Access & Network Modernization
Phase two focuses on implementing foundational zero trust capabilities. Identity infrastructure modernization typically takes priority, as identity verification underpins all subsequent access decisions. Deploy or upgrade IAM platforms to support modern authentication protocols, conditional access policies, and integration with security analytics.
Network modernization introduces micro-segmentation capabilities that contain lateral movement. This may involve deploying next-generation firewalls with application awareness, implementing software-defined networking, or adopting cloud-native network security controls. The goal is granular visibility and control over traffic flows between network segments.
Access modernization replaces broad network access with application-specific access. ZTNA solutions provide secure access to specific applications without granting network-level connectivity. This reduces attack surface while improving user experience compared to traditional VPN approaches.
Integration with existing software development practices ensures that new applications are designed with zero trust principles from inception. Development teams should incorporate security requirements into design reviews and implement authentication and authorization at the application layer rather than relying solely on network controls.
Phase 3 – Continuous Optimization & Risk-Based Controls
Mature zero trust implementations move beyond static policies to risk-based access decisions that adapt to changing threat conditions. Phase three integrates threat intelligence, behavioral analytics, and automation to enable dynamic policy enforcement.
Risk-based authentication adjusts verification requirements based on context. Low-risk access requests proceed with standard authentication, while high-risk scenarios trigger additional verification steps or require explicit approval. This balances security with user experience, applying friction only when risk warrants it.
Continuous optimization leverages operational data to refine policies. Monitor access patterns to identify overly permissive policies that could be tightened. Analyze authentication failures to detect potential attacks or user experience issues requiring remediation. Zero trust is not a destination but an ongoing program that evolves with the threat landscape.
Organizations should establish key performance indicators that track zero trust effectiveness. Metrics including mean time to detect threats, access decision accuracy, and user experience scores provide quantitative evidence of program value while identifying areas requiring improvement.
Decision Framework: Zero Trust Maturity Model
| Maturity Level | Characteristics | Typical Timeline | Key Milestones |
| Initial | Ad-hoc identity management, network-based access | Starting point | Security assessment complete |
| Developing | Centralized identity, basic MFA, initial segmentation | 6-12 months | SSO deployed, MFA enabled for privileged users |
| Defined | Consistent policies, device compliance checks, SIEM integration | 12-18 months | ZTNA pilot complete, micro-segmentation in critical zones |
| Managed | Risk-based access, automated response, continuous monitoring | 18-24 months | Full ZTNA deployment, automated threat response |
| Optimizing | AI-driven analytics, adaptive policies, proactive threat hunting | 24+ months | Predictive security analytics, continuous compliance |
Common Zero-Trust Implementation Challenges (and How GCC Leaders Solve Them)
Zero trust implementation is not without obstacles. Understanding common challenges and proven mitigation strategies helps enterprises avoid pitfalls that derail transformation initiatives.
Integrating Zero Trust with Legacy IAM, SIEM & SOC Tools
Most GCC enterprises have substantial investments in existing security infrastructure. Rip-and-replace approaches are costly, disruptive, and rarely necessary. Successful zero trust implementations integrate with legacy systems through federation, API connections, and phased migration strategies.
For IAM integration, evaluate whether existing identity providers can support modern authentication protocols and conditional access policies. Many legacy systems can be extended with additional components rather than replaced entirely. Where replacement is necessary, prioritize migration based on risk and business impact.
SIEM integration requires configuring zero trust components to forward relevant telemetry in formats that existing analytics platforms can process. Work with security operations teams to develop use cases and detection rules that leverage zero trust data. The goal is enhancing existing capabilities rather than creating parallel monitoring systems.
Consider the example of a regional telecom enterprise modernizing security without disrupting operations. By implementing zero trust controls progressively and maintaining interoperability with legacy systems, the organization enhanced security posture while preserving existing investments. This pragmatic approach applies across industries facing similar modernization pressures.
Managing Third-Party & Contractor Access Securely
Third-party access represents one of the highest-risk vectors for GCC enterprises engaged in digital transformation initiatives. Zero trust provides the framework for securing contractor and vendor access without impeding business operations.
Implement dedicated identity management for external users that applies zero trust principles consistently. Third-party accounts should receive only the access required for specific engagements, with automatic expiration dates and regular access reviews. Privileged access for contractors requires additional controls including session recording and just-in-time access provisioning.
Zero trust network access solutions enable application-specific access for third parties without exposing the broader network. Contractors accessing specific applications see only those applications, not the underlying infrastructure. This contains potential breaches and simplifies compliance with data protection requirements.
Organizations implementing manufacturing software development or other industrial solutions face particular challenges securing operational technology environments while enabling necessary vendor access for maintenance and support. Zero trust principles apply equally to IT and OT environments, though implementation approaches must account for operational constraints and legacy protocol requirements.
Cost, Skills Gap & Change-Management Barriers
Zero trust implementation requires investment in technology, training, and organizational change. Building realistic business cases that account for total cost of ownership while demonstrating risk reduction and compliance benefits secures executive support.
The cybersecurity skills shortage affects GCC organizations as acutely as other regions. Address skills gaps through a combination of training existing staff, engaging managed security service providers, and selective hiring for critical roles. Organizations should not delay zero trust implementation waiting for perfect internal capabilities.
Change management often determines implementation success more than technology choices. Users accustomed to broad network access may resist additional authentication requirements. Clear communication about security benefits, executive sponsorship, and responsive support for user issues helps manage this transition. Involve business stakeholders early to ensure zero trust controls support rather than impede business processes.
Engaging experienced implementation partners accelerates deployment while reducing risk. Partners with proven GCC experience understand regional compliance requirements, cultural considerations, and operational challenges that impact implementation success.
Benefits of Zero-Trust Security Architecture for GCC Enterprises
Zero trust implementation delivers measurable benefits across security, compliance, and operational dimensions that justify the investment required for transformation.
Reduced Breach Impact & Ransomware Containment
Micro-segmentation and least-privilege access dramatically limit the blast radius of successful breaches. When attackers compromise credentials or exploit vulnerabilities, zero trust controls prevent lateral movement to additional systems. This containment reduces the scope of incidents and accelerates recovery.
Ransomware attacks that would devastate flat networks face significant obstacles in zero trust environments. Without the ability to move laterally to additional systems, attackers cannot spread encryption to critical assets. This protection proves particularly valuable for GCC enterprises operating critical infrastructure or managing sensitive financial data.
The financial impact of breach containment extends beyond direct incident costs. Regulatory penalties, reputational damage, and business disruption costs all decrease when breaches are contained quickly. Zero trust investments generate measurable return through risk reduction that compounds over time.
Improved Visibility Across Users, Devices & Workloads
Zero trust implementations generate comprehensive telemetry that provides unprecedented visibility into enterprise operations. Security teams can see who accessed what resources, from which devices, and under what circumstances. This visibility supports both security monitoring and compliance reporting.
For enterprises managing distributed operations across multiple GCC nations, centralized visibility simplifies security operations while respecting local data residency requirements. Security teams can monitor access patterns across the enterprise while maintaining compliance with jurisdictional data handling requirements.
Enhanced visibility enables proactive security posture management. By analyzing access patterns and identifying anomalies before they become incidents, security teams shift from reactive incident response to proactive threat prevention. This operational maturity reduces both security risk and operational burden.
Faster Cloud Adoption with Stronger Security Posture
Zero trust architecture enables secure cloud adoption by extending consistent security controls from on-premises environments to cloud deployments. Rather than developing separate security approaches for each environment, organizations apply unified policies that work across hybrid and multi-cloud infrastructures.
This consistency accelerates cloud migration initiatives by removing security concerns that often delay transformation projects. When security controls travel with workloads, organizations can migrate applications confidently knowing that protection levels remain consistent.
Organizations pursuing cloud-native architecture trends benefit from zero trust principles embedded in their development and deployment processes. Security becomes an enabler of innovation rather than a constraint, supporting rapid iteration while maintaining protection levels appropriate to data sensitivity and compliance requirements.
Measurable ROI for CISOs & Boards
Board-level reporting requires demonstrable return on security investments. Zero trust implementations provide multiple metrics that demonstrate value: reduced incident response times, decreased audit preparation effort, improved compliance posture, and quantified risk reduction.
For GCC enterprises facing regulatory pressure and board scrutiny of cybersecurity investments, zero trust provides a framework for communicating security improvements in business terms. The continuous verification model generates data that supports objective assessment of security posture improvements over time.
Insurance considerations increasingly favor organizations with mature zero trust implementations. Cyber insurance underwriters recognize that zero trust controls reduce breach likelihood and impact, potentially resulting in more favorable coverage terms and premiums.
PAA / CXO Questions on Zero Trust Security Architecture
How Do You Implement Zero Trust Security Architecture?
Implementation begins with comprehensive assessment of current security posture, followed by phased deployment of identity-centric controls, network segmentation, and continuous monitoring capabilities. Start with identity infrastructure modernization, then extend to network access controls and application security. Most enterprises achieve initial zero trust capabilities within 12-18 months, with ongoing optimization continuing thereafter.
What Is the Cost of Implementing Zero Trust?
Cost varies significantly based on organizational size, existing infrastructure, and implementation scope. Enterprises should expect investment across technology licensing, integration services, training, and ongoing operations. Many organizations find that zero trust implementations replace rather than supplement existing tools, offsetting new investment with consolidated licensing. Build business cases that account for risk reduction, compliance simplification, and operational efficiency alongside direct costs.
Is Zero Trust Mandatory for GCC Compliance?
While regulations do not explicitly mandate "zero trust" terminology, the underlying principles align directly with GCC compliance requirements. SAMA, NCA, and NESA frameworks require identity management, access control, network security, and continuous monitoring capabilities that zero trust implementations provide. Organizations implementing zero trust find compliance evidence generation automated and audit preparation simplified.
What Industries Benefit Most from Zero Trust in the Middle East?
Banking, Financial Services & Insurance (BFSI) organizations face the most stringent regulatory requirements and greatest breach risk, making zero trust essential. Government and public sector entities managing citizen data and critical services benefit significantly. Energy, oil & gas companies protecting operational technology environments find zero trust controls valuable for securing converged IT/OT environments. Healthcare organizations protecting patient data and telecom enterprises managing vast subscriber information also represent priority sectors for zero trust adoption.
Is Your Organization Ready for Zero Trust?
Zero-Trust Readiness Checklist for GCC Enterprises
Organizations should assess their readiness across multiple dimensions before launching zero trust initiatives:
Identity Infrastructure: Do you have centralized identity management? Can you enforce multi-factor authentication consistently? Do you have visibility into privileged account usage?
Network Architecture: Can you implement micro-segmentation in your current environment? Do you have visibility into east-west traffic? Can you enforce application-aware access policies?
Cloud Environment: Do you have consistent security controls across on-premises and cloud deployments? Can you enforce data residency requirements through policy? Do you have visibility into cloud workload communications?
Security Operations: Can your SOC process additional telemetry from zero trust controls? Do you have use cases and runbooks for identity-centric monitoring? Can you respond to automated alerts from zero trust policy enforcement?
Organizational Readiness: Do you have executive sponsorship for zero trust transformation? Have you communicated changes to affected users? Do you have change management processes for security policy updates?
Key Questions CISOs Should Ask Before Selecting Vendors
When evaluating zero trust solutions for GCC deployment, CISOs should address several critical questions:
Does the solution support regional data residency requirements? Can it integrate with existing identity infrastructure? Does it provide the compliance reporting needed for SAMA, NCA, and NESA frameworks? Can it scale to support organizational growth and cloud expansion?
Evaluate vendor experience with GCC implementations specifically. Regional compliance requirements, data sovereignty constraints, and operational considerations differ from other markets. Vendors with proven GCC deployments understand these nuances and can accelerate implementation timelines.
Consider total cost of ownership beyond initial licensing. Implementation services, training requirements, ongoing support, and integration costs significantly impact on overall investment. Request reference customers from similar industries and regions to validate vendor claims and understand real-world implementation experiences.
Conclusion
Zero trust security architecture represents the essential framework for GCC enterprises navigating an increasingly hostile threat landscape while meeting stringent regulatory requirements. The principles of continuous verification, least-privilege access, and micro-segmentation address the fundamental weaknesses in legacy perimeter security that attackers exploit daily.
Implementation requires strategic planning, phased deployment, and organizational commitment. But the benefits—reduced breach impact, improved compliance posture, enhanced visibility, and secure cloud adoption—justify the investment for enterprises serious about protecting critical assets and maintaining stakeholder trust.
The question for GCC enterprise leaders is not whether to implement zero trust, but how quickly can their organizations begin the transformation. With regulatory enforcement tightening, threat sophistication increasing, and digital transformation accelerating, the window for proactive action narrows with each passing quarter.
VLink's cybersecurity services provide expertise, frameworks, and implementation support that GCC enterprises need to navigate zero trust transformation successfully. From initial assessment through ongoing optimization, our teams help organizations build security architectures that protect today while enabling tomorrow's digital initiatives.










 Shivisha Patel
Shivisha Patel

















