In today's rapidly evolving digital landscape, two sectors stand at the forefront of innovation and transformation: the automotive industry, with its burgeoning fleet of connected cars, and the manufacturing sector, undergoing a revolution powered by smart factories. While promising unprecedented efficiency, convenience, and connectivity, these advancements also introduce a complex web of cybersecurity vulnerabilities.
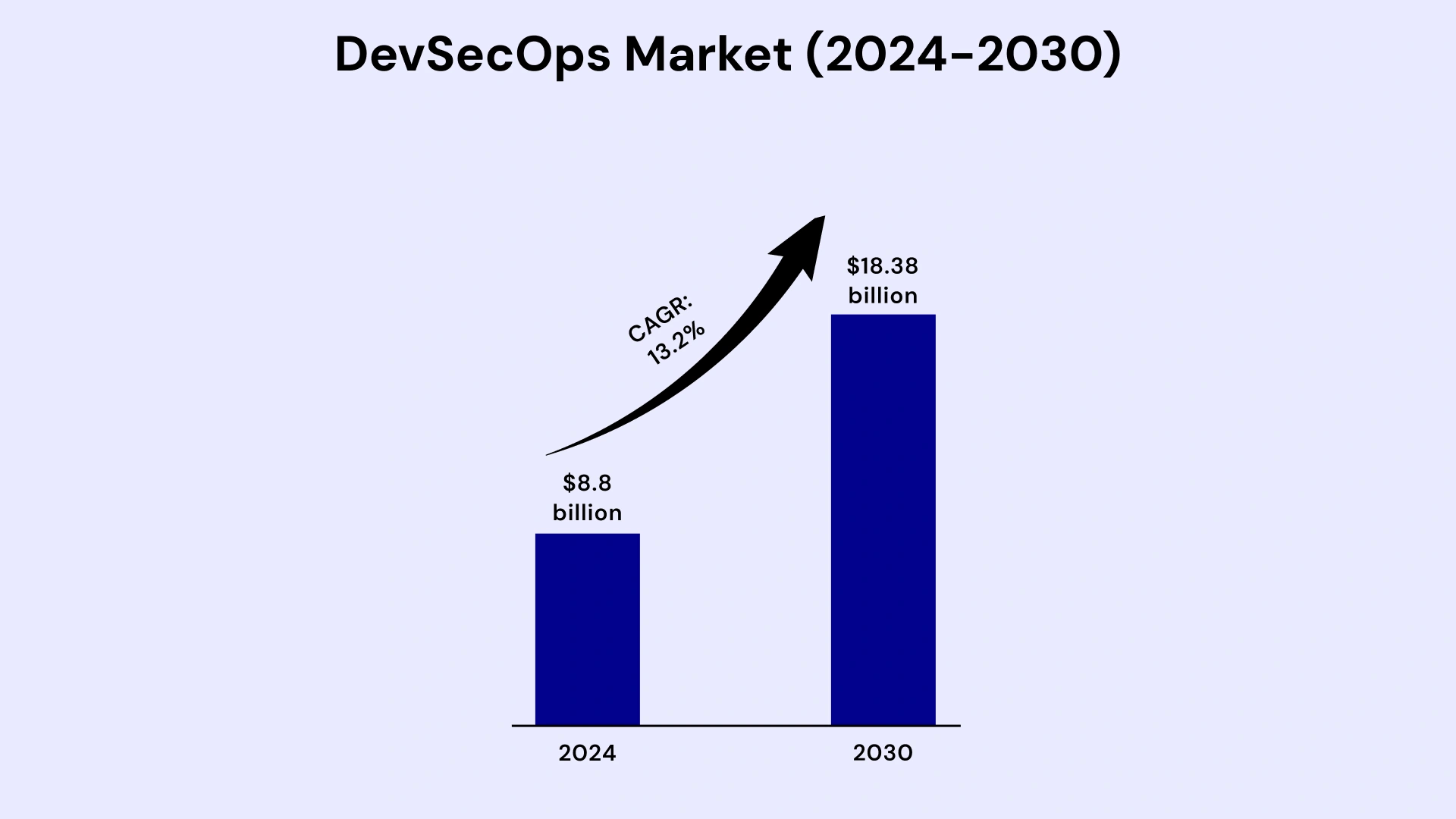
This surge is fueled by the growing demand for more secure, continuous application delivery and an increased focus on security and compliance. For startup owners and CXOs navigating this intricate terrain, integrating DevSecOps principles is no longer a luxury but a fundamental necessity for ensuring their ventures' safety, reliability, and long-term success.
This comprehensive blog delves deep into the critical role of DevSecOps in fortifying the digital infrastructure of connected cars and smart factories. We will explore the unique cybersecurity challenges inherent in each domain and examine the strategic implementation of DevSecOps.
The Expanding Threat Landscape: Cybersecurity in a Connected World
The convergence of IT and OT (Operational Technology) in connected cars and smart factories has blurred traditional security perimeters. While driving innovation, this interconnectedness also expands the attack surface, making these systems increasingly susceptible to sophisticated cyber threats.
Connected Cars: A Mobile Target
Modern vehicles are no longer just modes of transportation; they are becoming sophisticated computers on wheels. Cybersecurity for connected cars is paramount as these vehicles integrate many sensors, software, and communication systems. This intricate architecture presents numerous potential entry points for malicious actors.
Consider the risks:
- Remote Vehicle Control: Hackers could potentially gain unauthorized access to critical vehicle functions, such as braking, steering, and acceleration, posing a direct threat to passenger safety. Cybersecurity for connected vehicles must address these life-critical scenarios.
- Data Breaches and Privacy Violations: Connected cars collect vast amounts of data, including location, driving habits, and personal preferences. Failure to secure this data can lead to severe privacy violations and reputational damage.
- Theft and Manipulation: Cyberattacks can disable security systems, facilitate theft, or even manipulate vehicle identification numbers (VINs).
- Supply Chain Vulnerabilities: The complex supply chain involved in devops development services for automotive can introduce vulnerabilities at various stages, requiring robust DevSecOps in Automotive practices.
- Infotainment System Exploits: Seemingly benign infotainment systems can serve as gateways for attackers to infiltrate deeper vehicle networks. Smart cars and cybersecurity challenges often originate from these connected interfaces.
Smart Factories: Securing the Industrial Internet of Things
Smart factories, powered by the Industrial Internet of Things (IIoT), leverage interconnected devices, sensors, and software to optimize production processes. However, this increased connectivity also introduces significant cybersecurity challenges in smart manufacturing.
The potential consequences of a cyberattack on a smart factory are far-reaching:
- Disruption of Operations: Attacks targeting Industrial Control Systems (ICS) Security and Operational Technology Cybersecurity can halt production lines, leading to significant financial losses and supply chain disruptions.
- Data Theft and Intellectual Property Loss: Malicious actors can steal sensitive manufacturing data, including design specifications and production secrets.
- Tampering with Product Quality: Cyberattacks can manipulate production processes, leading to faulty or compromised products.
- Safety Hazards: In industrial environments, compromised systems can lead to dangerous malfunctions and potential harm to personnel. Securing IoT Devices in Smart Factories is crucial for preventing such incidents.
- Legacy System Integration: Integrating modern IIoT devices with older, less secure Industrial Control Systems (ICS) Security creates a complex security landscape.
DevSecOps: A Holistic Approach to Cybersecurity
In this interconnected and threat-filled environment, traditional security approaches that operate in silos are no longer sufficient. DevSecOps emerges as a critical paradigm shift, integrating security practices seamlessly into the entire software development lifecycle (SDLC), from initial design to deployment and operation.
What is DevSecOps?
DevSecOps is not merely bolting security onto existing DevOps workflows. It represents a fundamental cultural change emphasizing shared security responsibility across development, security, and operations teams. By integrating security early and continuously, DevSecOps aims to build secure systems by design, rather than addressing vulnerabilities as an afterthought.

Key Principles of DevSecOps:
- Security as Code: Treating security configurations and policies as code, allowing for automation, version control, and continuous integration.
- Shift Left: Integrating security practices earlier in the development lifecycle, identifying and mitigating vulnerabilities before they reach production.
- Continuous Feedback and Monitoring: Implementing constant monitoring and feedback loops to detect and respond to security threats in real-time.
- Collaboration and Communication: Fostering seamless cooperation and communication between development, security, and operations teams.
- Automation Testing: Automating security testing, vulnerability scanning, and compliance checks to improve efficiency and accuracy.
DevSecOps in Automotive: Building Secure Connected Cars
The automotive industry is rapidly embracing devops in car manufacturing to accelerate innovation and deliver new features to connected cars. However, this agility must be coupled with robust DevSecOps in Automotive practices to ensure connected car cybersecurity.
Implementing DevSecOps in Connected Cars:
- Secure Software Development Lifecycle (SSDLC): Integrating security considerations into every stage of the vehicle software development process, from requirements gathering to design, coding, testing, and deployment.
- Security Integration in CI/CD Pipelines: Automating security testing, such as static and dynamic code analysis, vulnerability scanning, and penetration testing, within the continuous integration and continuous delivery (CI/CD) pipelines. This ensures that security is a continuous process, not a one-time check.
- Threat Modeling: Proactively identifying potential threats and vulnerabilities in the vehicle's architecture and design to ensure connected car cybersecurity.
- Intrusion Detection and Prevention Systems (IDPS): Implementing systems within the vehicle to detect and respond to malicious activity in real-time.
- Over-the-Air (OTA) Security: Securing the OTA update mechanisms to prevent malicious updates from being installed on vehicles for connected car cybersecurity.
- Supply Chain Security: Implementing stringent security measures throughout the automotive supply chain to mitigate third-party components and software risks.
- Best Practices for DevSecOps in Automotive Industry: Adhering to industry-specific security standards and guidelines to ensure connected car cybersecurity.
Benefits of DevSecOps in Automotive:
- Enhanced Cybersecurity for Connected Cars and Cybersecurity for Connected Vehicles.
- Faster and more secure delivery of software updates and new features.
- Reduced risk of cyberattacks and associated financial and reputational damage.
- Improved compliance with industry regulations.
- Increased customer trust and confidence in the security of smart cars and cybersecurity challenges.
How DevSecOps Prevents Security Breaches in Connected Vehicle Software
DevSecOps in Automotive plays a crucial role in proactively preventing security breaches in connected car software through a multi-layered approach:
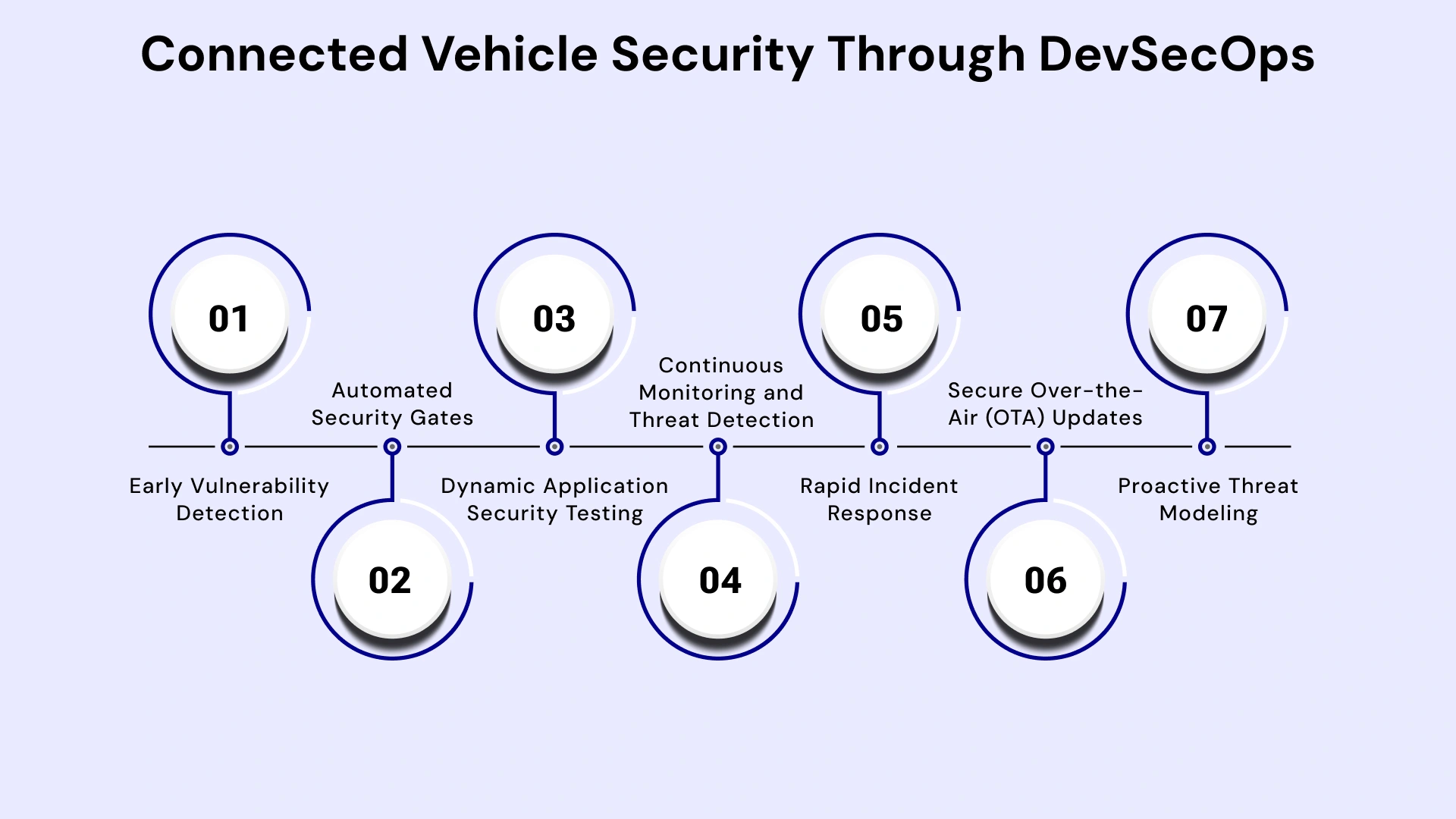
Early Vulnerability Detection:
By integrating security testing early in the DevOps development services lifecycle (Shift Left), DevSecOps identifies vulnerabilities in the design and code stages long before they reach production. Static Application Security Testing (SAST) and Software Composition Analysis (SCA) tools analyze code for potential flaws and identify vulnerable open-source components.
Automated Security Gates:
Security Integration in CI/CD Pipelines establishes automated security gates that prevent code deployment with known vulnerabilities. This ensures that only thoroughly tested and secure software progresses through the development pipeline.
Dynamic Application Security Testing (DAST):
During testing phases, DAST tools simulate real-world attacks on the application to identify runtime vulnerabilities that might not be apparent through static analysis. This helps in uncovering weaknesses in the deployed environment.
Continuous Monitoring and Threat Detection:
Once the software is deployed in connected cars, DevSecOps emphasizes continuous monitoring using Security Information and Event Management (SIEM) systems and Intrusion Detection and Prevention Systems (IDPS). This allows for the early detection of suspicious activities and potential breaches.
Rapid Incident Response:
In the event of a security incident, DevSecOps's collaborative nature facilitates a faster and more coordinated response. Security, development, and operations teams work together to contain the breach, remediate the vulnerabilities, and restore the system quickly, minimizing the impact.
Secure Over-the-Air (OTA) Updates:
DevSecOps Implementation in Connected Cars ensures the OTA update process is secure, preventing malicious actors from injecting compromised software into vehicles. This involves secure authentication, integrity checks, and encrypted communication channels.
Proactive Threat Modeling:
By conducting thorough threat modeling exercises, DevSecOps teams can proactively anticipate potential attack vectors specific to connected vehicles and design security controls to mitigate these risks. This helps in building resilience into the software architecture from the ground up.
DevSecOps for Smart Factories: Securing the Future of Manufacturing
The digital transformation of manufacturing relies heavily on the secure integration of IT and OT systems. DevSecOps for Smart Factories is crucial for protecting these complex and critical environments.
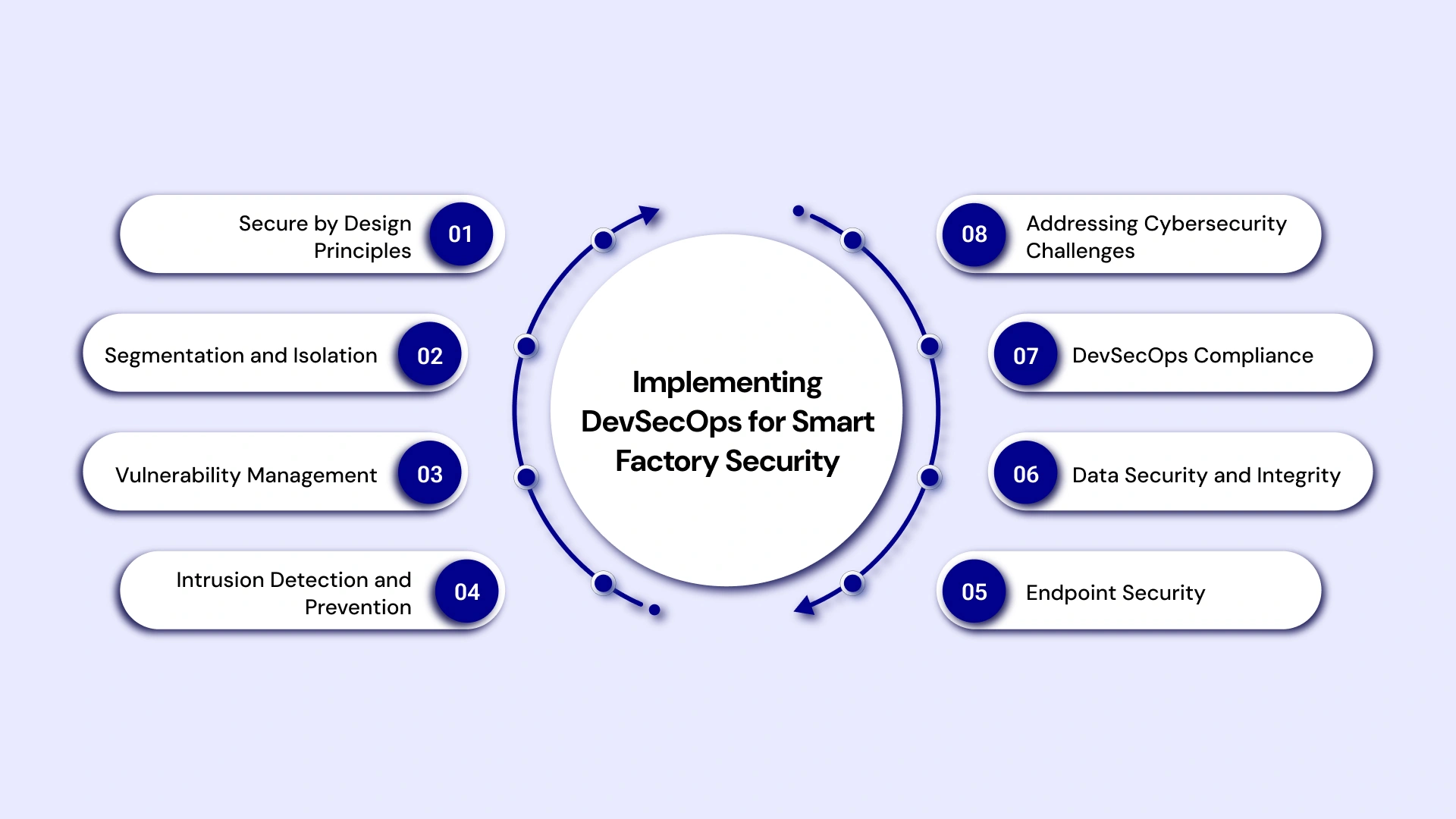
Implementing DevSecOps in Smart Factories:
- Secure by Design Principles: Building security into the architecture of smart factory DevSecOps solutions from the outset.
- Segmentation and Isolation: Critical OT networks should be isolated from less secure IT networks to limit the impact of potential breaches.
- Vulnerability Management: Implementing robust processes for identifying, assessing, and remediating IT and OT systems vulnerabilities.
- Intrusion Detection and Prevention for OT: Deploying specialized IDPS solutions for industrial protocols and environments.
- Endpoint Security for Industrial Devices: Securing individual IoT Devices in Smart Factories and industrial control systems.
- Data Security and Integrity: Implementing measures to protect sensitive manufacturing data's confidentiality, integrity, and availability.
- DevSecOps Compliance in Industrial Automation: Adhering to industry-specific regulations and standards, such as IEC 62443.
- Addressing Cybersecurity Challenges in Smart Manufacturing: Developing strategies to mitigate the unique security risks associated with interconnected industrial environments.
Benefits of DevSecOps in Smart Factories:
- Enhanced cybersecurity for smart factories and Industrial Internet of Things Security.
- Reduced risk of operational disruptions and financial losses.
- Protection of intellectual property and sensitive manufacturing data.
- Improved safety and reliability of industrial processes in cybersecurity for Smart Factories.
- Enhanced compliance with regulatory requirements.
- Effective Securing IoT Devices in Smart Factories.
Compliance and Regulatory Landscape in Automotive Cybersecurity
The automotive industry operates under stringent regulatory and compliance frameworks concerning safety and data privacy. DevSecOps in Automotive plays a vital role in ensuring compliance with key standards and regulations:
ISO 26262 ("Road vehicles – Functional safety"):
This standard addresses the functional safety of electronic vehicle systems. While primarily focused on preventing hazards due to malfunctions, it has significant implications for cybersecurity, as cyberattacks can also lead to safety-critical failures. DevSecOps Implementation in Connected Cars helps build secure software that contributes to the overall functional safety of the vehicle by preventing malicious manipulation of critical systems.
ASPICE (Automotive SPICE - Software Process Improvement and Capability Determination):
ASPICE is a framework for assessing and improving software development processes in the automotive industry. Integrating security activities throughout the ASPICE process, as advocated by DevSecOps, ensures that security is not an afterthought but an integral part of building high-quality and secure automotive software.
GDPR (General Data Protection Regulation):
GDPR compliance is mandatory for vehicles sold in Europe or handling the personal data of EU citizens. DevSecOps practices help implement security measures to protect the personal data collected and processed by connected cars, such as location data, driving behavior, and infotainment system usage. This includes data encryption, access controls, and secure data storage.
NHTSA (National Highway Traffic Safety Administration):
The NHTSA plays a crucial role in vehicle safety regulations in the United States. While specific cybersecurity regulations are evolving, the NHTSA emphasizes the importance of cybersecurity in ensuring vehicle safety. DevSecOps aligns with the NHTSA's focus on proactive security measures and rapid response to vulnerabilities in Cybersecurity for Connected Vehicles.
Other Regional and Industry-Specific Regulations:
Automotive manufacturers must comply with other regional or industry-specific cybersecurity guidelines and standards depending on the target market. DevSecOps Compliance in Industrial Automation principles can be adapted to the automotive context to ensure adherence to these diverse requirements.
By embedding security into the development lifecycle, DevSecOps enables automotive companies to build software that meets functional requirements and adheres to these critical compliance standards, reducing the risk of legal penalties and reputational damage.
Real-World Security Case Studies in Automotive Cybersecurity
Examining real-world security incidents highlights the critical need for robust DevSecOps practices in the automotive industry:
The Jeep Cherokee Hack:
Researchers remotely exploited a vulnerability in the Jeep Cherokee's Uconnect infotainment system, demonstrating the ability to control critical vehicle functions like steering, braking, and transmission. This incident underscored the potential safety risks associated with insecure connected car software and the importance of secure design and testing—key tenets of DevSecOps Implementation in Connected Cars.
Nissan LEAF Telematics Hack:
Security researchers discovered a vulnerability in their telematics system, allowing them to remotely access and control certain vehicle functions, such as climate control. This highlighted the risks associated with insecure APIs and the need for rigorous security testing throughout the development process, a core component of DevSecOps.
Keyless Entry System Vulnerabilities:
Numerous studies have revealed vulnerabilities in keyless entry systems that allow thieves to unlock and even start vehicles remotely. This emphasizes the importance of secure communication protocols and robust authentication mechanisms, which can be ensured through a Secure Software Development Lifecycle guided by DevSecOps principles.
Attacks on Automotive Suppliers:
Cyberattacks targeting automotive suppliers can significantly ripple effects on the entire industry. In some cases, attackers have gained access to sensitive design data and even disrupted production. This underscores the need for strong supply chain security measures, integrated within a DevSecOps in Automotive framework.
Emerging Threats to Autonomous Vehicles:
New cybersecurity challenges emerge as vehicles become increasingly autonomous. Attacks targeting sensor data, decision-making algorithms, and communication systems could have catastrophic consequences. Smart cars and cybersecurity challenges in this domain necessitate a proactive DevSecOps approach to building resilient and secure autonomous driving systems.
These real-world examples demonstrate the tangible risks associated with inadequate cybersecurity in connected cars and highlight how the proactive and integrated approach of DevSecOps can significantly reduce the likelihood and impact of such incidents. By embedding security throughout the development lifecycle, automotive companies can build more resilient and trustworthy vehicles for the future.
DevSecOps Implementation Strategy: A Roadmap for Success
Implementing DevSecOps effectively requires a well-defined strategy that addresses the specific needs and challenges of the automotive and smart factory sectors. Here's a comprehensive DevSecOps implementation strategy:
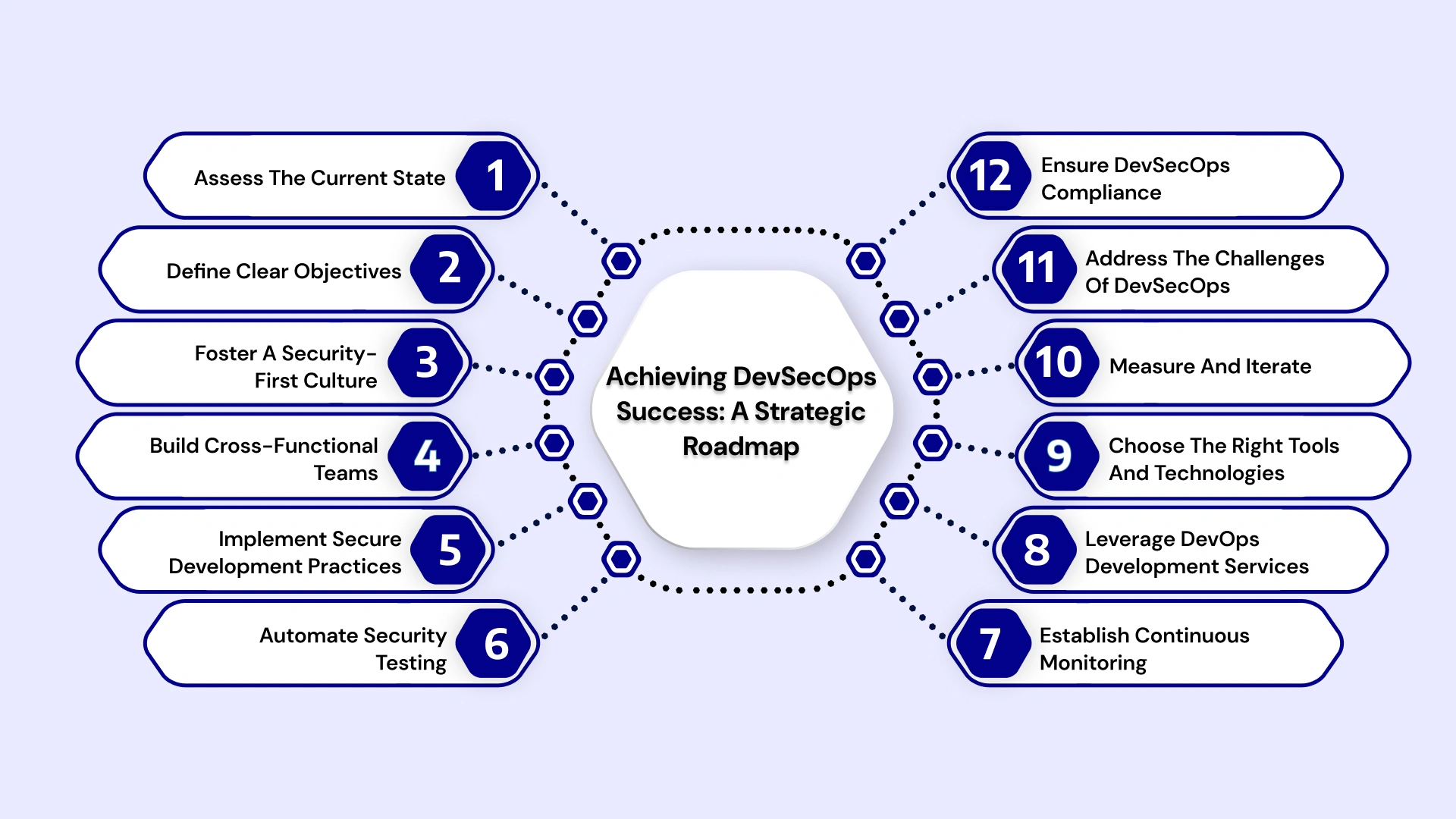
- Assess the Current State: Evaluate the existing development and security processes, identify gaps, and understand the cybersecurity challenges within the context of connected cars or smart factories.
- Define Clear Objectives: Establish specific, measurable, achievable, relevant, and time-bound (SMART) goals for DevSecOps implementation. These objectives should align with the business goals and address key cybersecurity risks.
- Foster a Security-First Culture: Cultivate a culture of shared responsibility for security across all teams. This involves training, awareness programs, and empowering individuals to prioritize security in their daily tasks.
- Build Cross-Functional Teams: Establish integrated teams comprising development, security, and operations personnel. This fosters better communication, collaboration, and a shared understanding of security requirements.
- Implement Secure Development Practices: Integrate security into every stage of the SDLC. This includes threat modeling, secure code reviews, and static and dynamic code analysis.
- Automate Security Testing: Integrate automated security testing tools into the CI/CD pipelines to ensure continuous security assessment. This includes vulnerability scanning, penetration testing, and compliance checks.
- Establish Continuous Monitoring and Incident Response: Implement robust monitoring tools and processes to detect and respond to security incidents in real-time. Develop a clear incident response plan.
- Leverage DevOps Development Services: Consider partnering with experienced providers to accelerate DevSecOps implementation and gain access to specialized expertise.
- Choose the Right Tools and Technologies: Select security tools and technologies that integrate seamlessly with the existing development and operations infrastructure.
- Measure and Iterate: Continuously monitor the effectiveness of the DevSecOps implementation, track key metrics, and make necessary adjustments to improve the process.
- Address the challenges of DevSecOps: Recognize and proactively address the unique hurdles associated with implementing DevSecOps in industrial environments, such as legacy systems and OT-specific security concerns.
- Ensure DevSecOps Compliance in Industrial Automation: Stay informed about and adhere to relevant industry regulations and standards.
The Evolving Future of DevSecOps for Connected Cars and Smart Factories
The future of DevSecOps is vital for the increasingly complex security of connected cars and smart factories.
- Expect deeper AI/ML integration for smarter threat detection and automated responses.
- Predictive analytics will anticipate threats, enabling proactive defense in both sectors.
- Automation will expand across development and operations, including specialized OT environments.
- Zero Trust architectures will become more prevalent, enhancing security through strict verification and segmentation.
- DevSecOps will cover the entire automotive vehicle lifecycle, focusing on secure OTA updates.
- In smart manufacturing, OT-specific DevSecOps tools and methods will evolve. Collaboration and shared responsibility will deepen.
- Standardized frameworks and a stronger focus on supply chain security will emerge as best practices.
Ultimately, the future of DevSecOps is about continuous adaptation, leveraging advanced technologies, and fostering a strong security culture to build resilient and secure connected cars and smart factories against evolving cyber threats.
Pro Tips:- Navigating the complexities of DevSecOps and cybersecurity can be daunting for startup owners and CXOs. Engaging with a reputable cybersecurity service provider or leveraging cybersecurity consulting services can provide invaluable expertise and support.
When selecting a partner, consider their experience in the automotive or industrial sectors, their understanding of DevSecOps principles, and their track record of delivering effective security solutions.
VLink: Your Dedicated DevSecOps Ally for Unbreakable Cybersecurity
If you're building the future with connected cars and smart factories, that's awesome! But in this super-connected world, keeping things secure isn't just a good idea—it's everything. That's where VLink comes in as your dedicated cybersecurity service provider and DevOps consulting services partner, laser-focused on DevSecOps.
Think of us as your expert co-pilot in navigating the cybersecurity challenges unique to the automotive and manufacturing realms. We speak the language of DevSecOps in Automotive, understanding the critical need for standards like ISO 26262 and ASPICE. We're equally fluent in the security demands of DevSecOps for Smart Factories, where Industrial Control Systems (ICS) Security is paramount.
Why team up with VLink for your DevSecOps journey?
- We "get" Automotive and Manufacturing Security: We're not just generic security folks. We have deep-dive knowledge of what makes cybersecurity for cars and smart factories tick – and what makes them vulnerable.
- We're with you every step of the way: From mapping out your DevSecOps implementation strategy to weaving security into your daily development flow (Security Integration in CI/CD Pipelines), we're your trusted guide to building a rock-solid Secure Software Development Lifecycle.
- Threat? Not on our watch! We're all about being proactive. Our threat-modeling ninjas help you see potential attacks on your connected vehicles and show you how to keep those Securing IoT Devices in Smart Factories. We set up smart defenses (Operational Technology Cybersecurity) to keep the bad guys out.
- Automation is our superpower. We use smart tools to automate security checks, find weaknesses, and ensure compliance without slowing down your excellent DevOps development services.
- Compliance? Sorted! We know the rules – GDPR, ISO 26262, you name it. We help you tick all the boxes so you can focus on innovating.
- Solutions built for you: We know smart factories aren't the same as connected cars. We craft Smart Factory DevSecOps Solutions and DevSecOps Implementation in Connected Cars that fit your needs, whether you're worried about Industrial Internet of Things Security or the latest smart cars and cybersecurity challenges.
- Expert help, always: Our cybersecurity consulting services team is packed with experienced pros who live and breathe security. We're here to share our knowledge and help you build a fortress.
- We tackle the tough stuff: Our dedicated team knows the challenges of DevSecOps in Smart Factories and the automotive world are real, like securing older systems and complex supply chains. We've got strategies to handle them.
Conclusion: Embracing DevSecOps for a Secure Future
The future of both the automotive and manufacturing industries is inextricably linked to connectivity and digitalization. However, this progress must be underpinned by a strong foundation of cybersecurity. DevSecOps provides the essential framework for building secure connected cars and smart factories by integrating security seamlessly into the development lifecycle.
By embracing DevSecOps, startup owners and CXOs can mitigate the growing cybersecurity challenges, protect their assets and customers, and build resilient and trustworthy systems. Investing in DevSecOps implementation is not just a security imperative; it is a strategic investment in their businesses' long-term success and sustainability in an increasingly connected world.
Integrating DevSecOps in automotive and DevSecOps for smart factories is the key to unlocking the full potential of these transformative technologies while ensuring a secure and prosperous future. Ready to make your connected cars and smart factories virtually impenetrable? VLink is your dedicated DevSecOps ally. Connect with us now and discuss how we can help you build a secure and innovative future!









 Shivisha Patel
Shivisha Patel

















