Third-party vendors have quietly become the most exploited entry point for cyberattacks targeting GCC enterprises. What was once a routine procurement decision now carries board-level consequences that CISOs and CXOs cannot afford to ignore.
This playbook addresses these friction points directly. It provides GCC CXOs with a structured approach to third-party vendor risk management that balances regulatory compliance with operational velocity—transforming vendor onboarding from a security bottleneck into a competitive advantage. Organizations looking to strengthen their overall security posture can explore comprehensive cybersecurity consulting services that address these challenges systematically.
Why Third-Party Vendors Are Now the No.1 Cyber Risk Vector in the GCC
From Procurement Risk to Board-Level Cyber Risk
The conversation around vendor risk has fundamentally shifted over the past decade. Previously, procurement teams evaluated vendors primarily on cost, capability, and delivery timelines. Cybersecurity considerations, if present at all, occupied a small checkbox on lengthy RFP documents that rarely received meaningful scrutiny.
Today, that checkbox has expanded into a board-level agenda item demanding executive attention. High-profile supply chain breaches—including incidents affecting major software providers and managed service organizations—have demonstrated that a single compromised vendor can cascade into operational disruptions, regulatory penalties, and reputational damage worth millions of dollars. For GCC enterprises, where government contracts and critical infrastructure projects demand impeccable security postures, the stakes are considerably higher than global averages.
Regional data reinforces this urgency. Approximately 15% of Middle East organizations reported data breaches costing more than $100,000 in the past year, with 13% exceeding $1 million in direct costs alone. Third-party relationships contributed significantly to these incidents. The vendors providing cloud services, SaaS applications, managed IT support, and specialized consulting often possess privileged access to sensitive systems—access that sophisticated attackers actively target through supply chain compromise techniques.
.
GCC-Specific Threat Amplifiers: Cloud, SaaS, IoT & OT Ecosystems
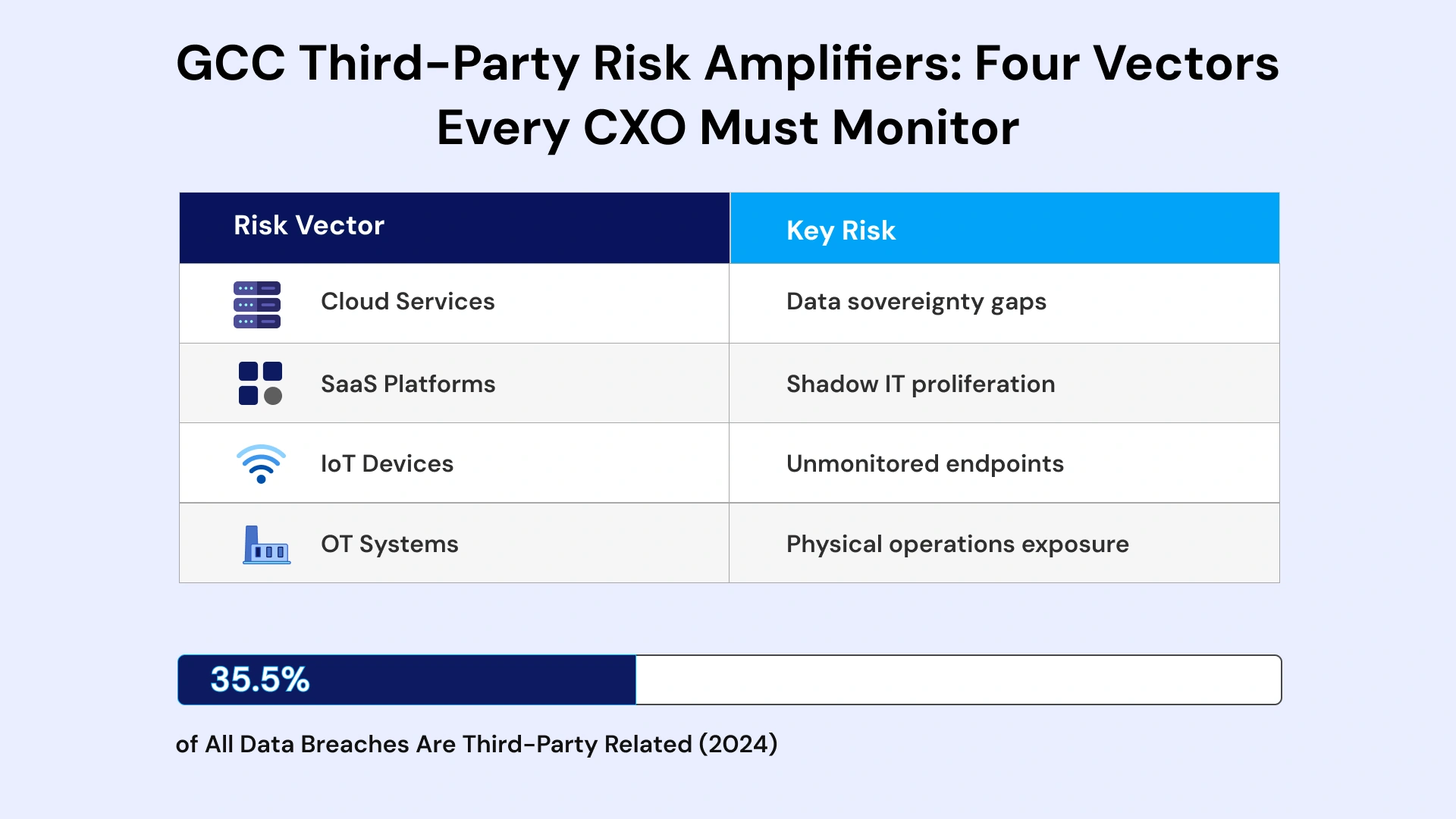
Several factors unique to the GCC region amplify third-party cybersecurity risk beyond global norms, creating a threat environment that demands localized strategies.
Cloud adoption across UAE and Saudi Arabia has accelerated rapidly, driven by Vision 2030 initiatives, smart city programs, and digital government transformation mandates. Every cloud service provider, every SaaS platform, and every managed service arrangement introduces external entities with varying security maturity levels into enterprise environments. The speed of adoption has frequently outpaced security governance frameworks designed for traditional on-premises architectures.
Critical infrastructure sectors—energy, utilities, aviation, ports, and telecommunications—face compounded challenges that intersect physical and digital risk. These industries increasingly integrate IoT sensors and operational technology (OT) systems managed by specialized vendors who may lack enterprise-grade security practices. A compromised maintenance contractor or equipment supplier can provide adversaries with pathways into systems controlling physical operations, potentially affecting national security interests.
Data sovereignty requirements add another layer of complexity to vendor relationships. Saudi Arabia's Personal Data Protection Law (PDPL) and UAE's Federal Data Protection Law impose strict obligations around data residency and cross-border transfers. Vendors unable to guarantee local data handling face immediate disqualification from sensitive projects—yet verifying these claims during onboarding remains challenging for many enterprises lacking specialized due diligence capabilities.
Organizations implementing zero-trust security architecture find themselves better positioned to manage these regional threat amplifiers through continuous verification rather than perimeter-based trust assumptions.
The Hidden Cybersecurity Risks Lurking in Vendor Onboarding
Shadow IT and Unvetted SaaS Vendors
Shadow IT represents one of the most persistent blind spots in enterprise vendor risk management programs. Business units, under pressure to deliver results quickly and meet aggressive project timelines, often adopt SaaS tools without routing them through security review processes. A marketing team subscribes to a new analytics platform to track campaign performance. Finance implements a specialized reporting tool to accelerate month-end closing. HR deploys a recruitment management system to streamline hiring workflows. Each decision seems innocuous individually and often goes undetected by central IT governance.
Collectively, these unvetted applications create significant exposure that compounds over time. They may store sensitive customer data, integrate with core systems via APIs, process payment information, and operate entirely outside established security monitoring and incident response protocols. When incidents occur, security teams discover these shadow applications only during forensic investigation—far too late to prevent damage or contain breaches effectively.
Over-Reliance on Tick-Box Compliance
Many enterprises fall into the trap of equating compliance with security—a dangerous conflation that creates false confidence. A vendor presents ISO 27001 certification during the RFP process. Another provides SOC 2 Type II reports with clean auditor opinions. Procurement teams check the compliance boxes and proceed with onboarding, believing they have adequately addressed cybersecurity risk.
This approach fundamentally misunderstands the nature of cybersecurity risk in dynamic threat environments. Compliance frameworks establish minimum baselines and document control implementations at specific points in time—they do not guarantee ongoing protection against sophisticated, evolving attacks. Numerous breached organizations maintained full compliance certifications at the time of compromise. The certificates demonstrated adherence to documented controls during audit windows; they did not reveal whether those controls remained effective against current threats or whether implementation had degraded since certification.
Fourth-Party & Supply Chain Blind Spots
Vendor risk assessments traditionally focus on direct relationships: the cloud provider hosting enterprise applications, the software vendor supplying business systems, the managed service provider handling IT operations. Yet these vendors themselves rely on their own extensive supply chains—fourth parties whose security practices remain largely invisible to the enterprise, but whose compromises can cascade upstream.
A software vendor may outsource code development to subcontractors in multiple geographies. A cloud provider may route data through third-party infrastructure for load balancing or disaster recovery. A SaaS platform may embed components from dozens of open-source projects with varying maintenance levels and security practices. Each layer introduces additional risk that standard due diligence processes rarely capture or even acknowledge.
Hidden Vendor Risk Categories and Mitigation Approaches
| Risk Category | Business Impact | Mitigation Approach |
| Shadow IT/Unvetted SaaS | Data exposure, compliance gaps, unmonitored access | CASB deployment, vendor discovery tools, policy enforcement |
| Tick-Box Compliance | False security confidence, audit failures | Continuous monitoring, technical validation, penetration testing |
| Fourth-Party Exposure | Supply chain attacks, cascading breaches | Subcontractor disclosure requirements, supply chain mapping |
GCC Regulatory Reality: Why Compliance Alone Is Not Enough
Navigating NCA, NESA, SAMA & UAE Data Protection Laws
GCC enterprises operate under an increasingly complex and evolving regulatory landscape that demands specialized expertise to navigate effectively. Understanding the key frameworks—and their vendor-specific requirements—is essential for CXOs leading cybersecurity strategy across the region.
GCC Cybersecurity Regulatory Frameworks Comparison
| Framework | Jurisdiction | Key Vendor Requirements | Primary Sectors |
| NCA ECC | Saudi Arabia | Third-party risk assessments, data localization, documented controls | Government, Critical Infrastructure |
| SAMA CSF | Saudi Arabia | Vendor due diligence, 6-hour breach notification, regular assessments | Banking, Financial Services, Insurance |
| NESA IAS | UAE | Information security controls, vendor audits, incident reporting | Critical Sectors, Government Entities |
| UAE Federal DPL | UAE | Data processor agreements, cross-border transfer restrictions | All Sectors Processing Personal Data |
Where Most Enterprises Fail Audits Despite Being "Compliant"
Audit failures frequently occur not from lack of controls, but from implementation gaps and documentation deficiencies that compliance checklists fail to capture during self-assessments. Understanding these common failure points helps CXOs focus remediation efforts effectively.
Common failure points include incomplete vendor inventories where security teams cannot account for all third-party relationships across the enterprise, outdated risk assessments that reflect vendor security postures from initial onboarding rather than current operational states, and missing contractual provisions around right-to-audit clauses, breach notification requirements, and data handling obligations.
Documentation gaps present another persistent challenge across GCC organizations. Enterprises may implement strong technical controls but lack the evidence trails and audit documentation that regulatory examiners require. When SAMA, NCA, or NESA auditors request proof of vendor security reviews, organizations struggle to produce consistent records across their vendor ecosystem spanning months or years of relationship management.
Organizations seeking to strengthen their governance, risk, and compliance (GRC) programs benefit from systematic approaches that embed documentation requirements into operational workflows rather than treating compliance as a separate activity.
A CXO Decision Framework: The GCC Vendor Cyber-Gate Model
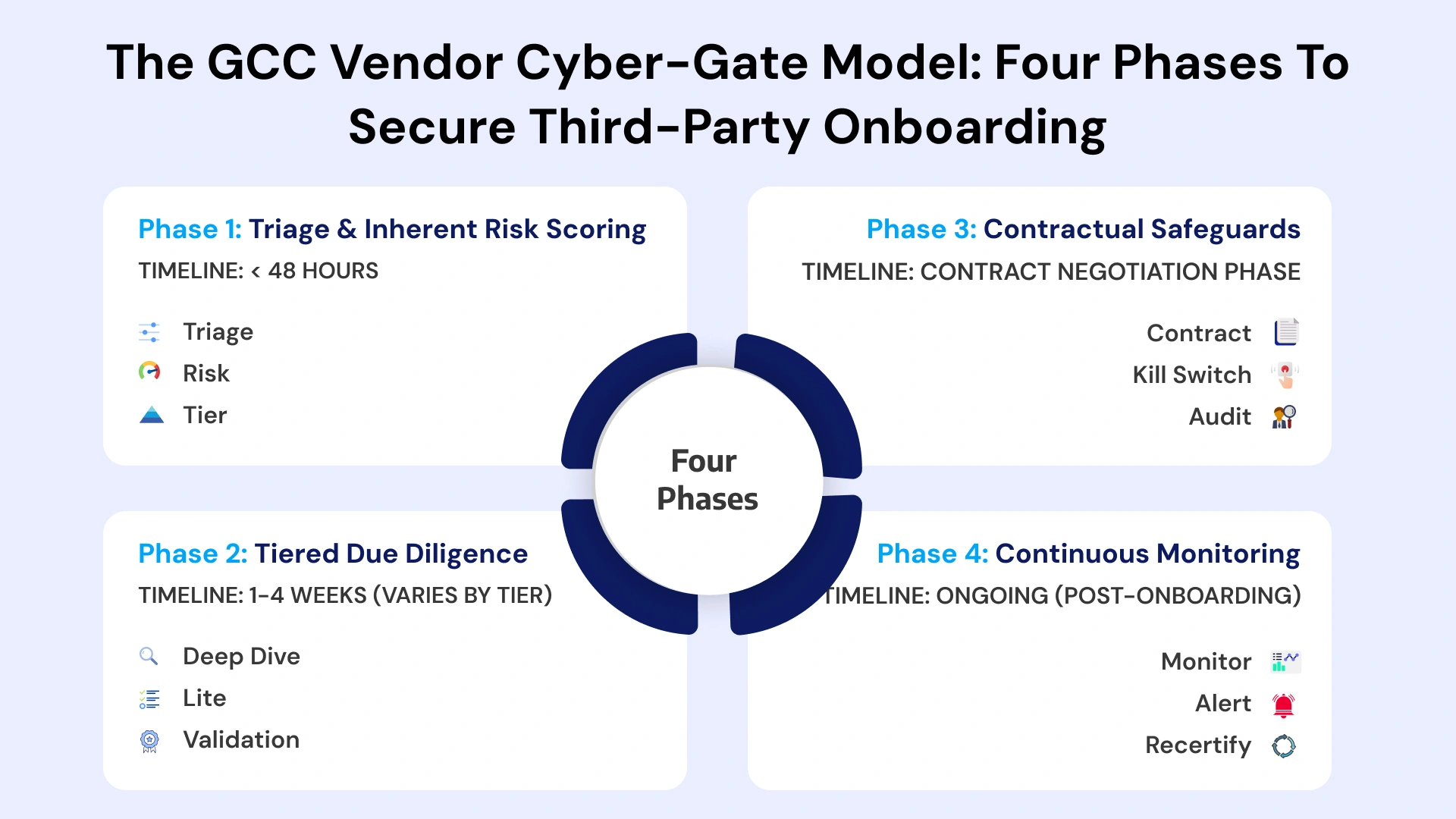
Effective third-party risk management in GCC enterprises requires a structured approach that balances assessment thoroughness with operational efficiency. The Vendor Cyber-Gate Model provides this structure through four distinct phases, each designed to address specific risk management objectives while maintaining business velocity and avoiding unnecessary bottlenecks for low-risk vendor relationships.
Phase 1: Vendor Triage & Inherent Risk Scoring
The first phase establishes rapid categorization of vendors based on inherent risk factors before detailed assessments consume significant resources. Within 48 hours of vendor identification, procurement teams input basic parameters into the triage system: service type, data access requirements, operational criticality, system integration depth, and geographic considerations.
Automated logic applies predetermined rules aligned with regulatory requirements and organizational risk appetite. Vendors handling Saudi National Data or UAE Personal Data receive automatic Tier 1 (Critical) classification regardless of other factors. Those accessing production systems, possessing privileged credentials, or integrating with core business applications fall into Tier 2 (High). Vendors with limited data access, no system integration capabilities, and purely advisory or non-technical roles populate Tier 3 (Low) categories.
Phase 2: Tiered Due Diligence (Lite vs Deep Dive)
Due diligence intensity scales according to vendor tier classification established in Phase 1, ensuring assessment effort matches actual risk exposure.
Tier 1 vendors undergo comprehensive evaluation including regulatory compliance verification against NCA ECC or NESA requirements as applicable, technical audits with recent penetration testing reports and vulnerability assessments, financial health assessments to evaluate business continuity and operational resilience risk, fourth-party risk disclosure requirements documenting significant subcontractors, and on-site or virtual security assessments for highest-criticality relationships.
Tier 3 vendors follow a streamlined "Lite" process designed for efficiency: automated external security rating checks through platforms like Security Scorecard or BitSight providing objective baseline data, simplified questionnaires focusing on fundamental hygiene (multi-factor authentication, backup procedures, incident response capabilities, employee security awareness), and self-attestation for basic security controls with periodic verification sampling.
This tiered approach prevents assessment bottlenecks that frustrate business units while maintaining appropriate rigor for relationships that genuinely warrant detailed examination.
Phase 3: Contractual Safeguards & Kill Switches
Contractual provisions establish the legal and operational boundaries of vendor relationships, providing enforcement mechanisms when technical controls prove insufficient. Essential clauses for GCC enterprises include several critical elements that legal and security teams must coordinate to implement effectively.
Right-to-Audit provisions enable enterprise inspection of vendor security logs, control implementations, and incident response procedures with reasonable notice periods. Data Sovereignty confirmations provide explicit, legally binding guarantees that data will not leave UAE or KSA borders without prior written approval and documented justification. Breach Notification SLAs aligned with regulatory requirements mandate immediate vendor notification—SAMA requires financial institutions to receive alerts within 6 hours for significant incidents affecting their data or systems. Termination provisions allowing immediate contract cancellation for material security breaches or compliance failures without standard notice periods or penalty provisions.
These contractual "kill switches" provide enterprises with enforcement mechanisms when vendor security postures deteriorate, incidents occur, or regulatory requirements change in ways that affect vendor compliance status.
Phase 4: Continuous Monitoring Beyond Onboarding
Vendor risk management extends far beyond initial onboarding assessments—it requires ongoing vigilance throughout relationship lifecycles. Continuous monitoring programs track vendor security postures using multiple data sources and trigger mechanisms.
Trigger events initiate immediate review protocols regardless of scheduled assessment cycles. These include significant drops in external security ratings (typically 10+ point declines on common rating platforms), public breach disclosures or regulatory enforcement actions affecting the vendor, leadership changes in security or technology functions, mergers, acquisitions, or significant organizational restructuring, and threat intelligence indicating active targeting of the vendor's industry or technology stack.
Annual recertification processes automate the re-sending of compliance questionnaires, ensuring documentation remains current and reflecting actual current-state controls rather than historical implementations. For Tier 1 vendors, quarterly reviews examine ongoing compliance with contractual security requirements and regulatory obligations, supported by evidence collection and validation.
What Leading UAE and Saudi Enterprises Are Doing Differently
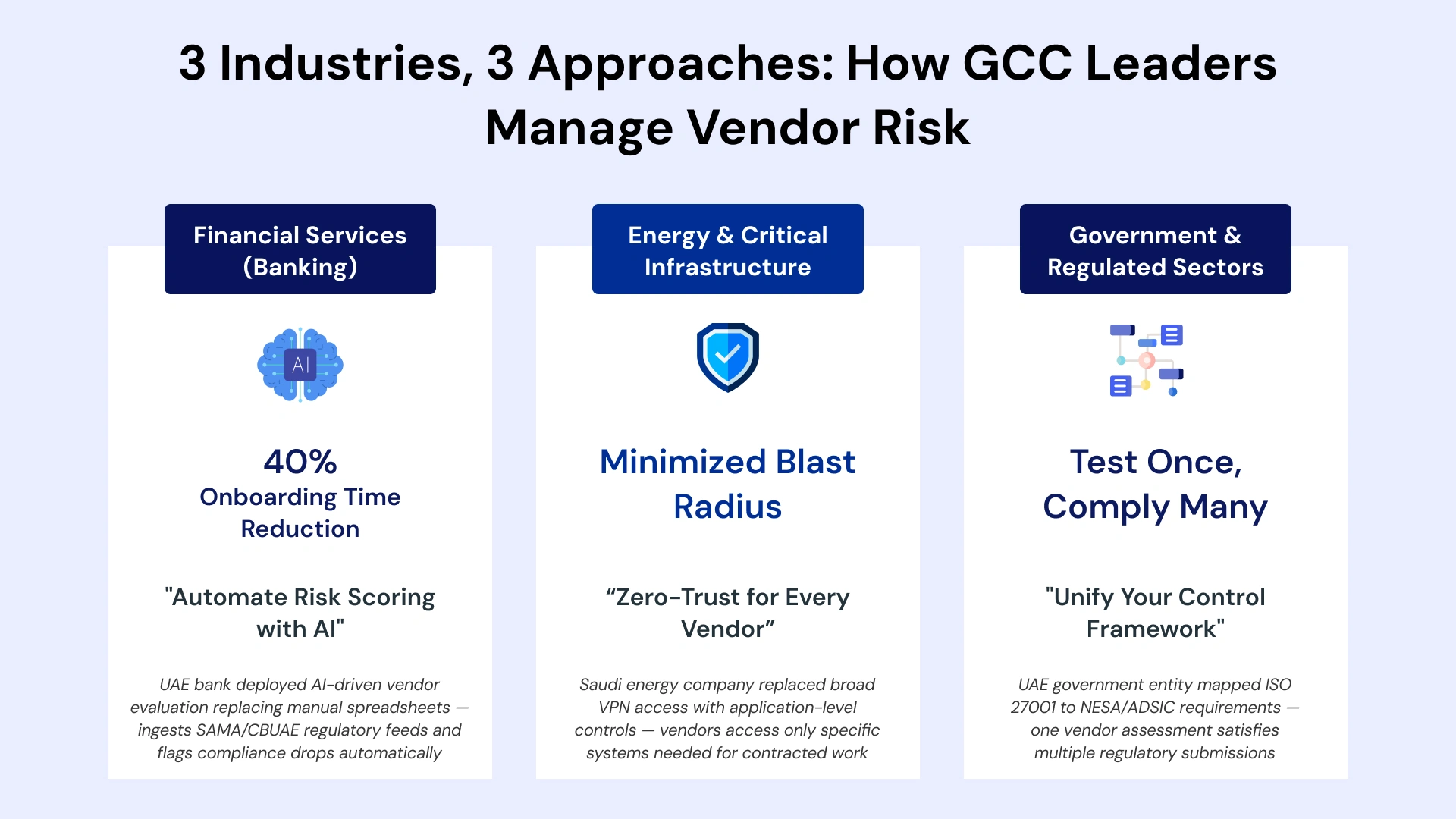
Financial Services: AI-Driven Vendor Risk Scoring
A leading UAE bank transformed its vendor risk assessment process by deploying AI-driven evaluation systems that fundamentally changed operational efficiency. The legacy approach—manual spreadsheet assessments, email-based evidence collection, and periodic annual reviews—created significant bottlenecks that frustrated business stakeholders. Vendor onboarding timelines stretched to weeks or even months for complex relationships, delaying critical initiatives and creating shadow IT pressures.
The new system ingests vendor data feeds from multiple sources, regulatory updates from SAMA and the Central Bank of UAE, external threat intelligence, and continuous security rating data. Machine learning algorithms continuously score vendors against predefined risk thresholds calibrated to the bank's specific risk appetite and regulatory obligations. When vendors drop below compliance standards or exhibit concerning security posture changes, the system automatically flags relationships for immediate human review.
Results validated the investment: 40% reduction in average onboarding time for new vendors, improved fraud detection through real-time vendor monitoring, and significantly reduced manual workload for the GRC team enabling focus on strategic initiatives rather than routine data collection.
Organizations exploring similar capabilities often leverage AI development services to build customized risk scoring engines aligned with regional regulatory requirements and organizational risk frameworks.
Energy & Critical Infrastructure: Zero-Trust for Third-Party Access
A major Saudi energy company recognized that traditional perimeter-based security models fundamentally failed to address third-party access risks in operational technology environments. Maintenance contractors, equipment suppliers, specialized engineering consultants, and system integrators all required access to operational technology systems—access that legacy VPN solutions provided far too broadly, granting network-level connectivity that attackers could exploit.
The organization implemented zero-trust architecture specifically designed for third-party interactions, treating every access request as potentially hostile regardless of source network. Instead of granting broad network access through VPN tunnels, identity management systems restrict vendors to only the specific applications and data sets required for their contracted work. Every access request undergoes real-time authentication and authorization checks against current entitlement policies.
Government & Regulated Sectors: Unified Control Frameworks
GCC government entities face unique compliance challenges stemming from multiple overlapping frameworks with similar but not identical requirements. A prominent UAE government organization found that managing NESA, ADSIC (Abu Dhabi Systems and Information Centre), and sector-specific requirements independently created unsustainable workloads for both internal teams and vendor partners. Vendors answered essentially identical security questions multiple times for different regulatory submissions, creating frustration and inefficiency.
The solution: a Unified Control Framework (UCF) mapping common controls across regulations to eliminate redundant assessment activities. ISO 27001 requirements align with NESA provisions; NCA ECC controls map to international standards; sector-specific requirements layer on top of this common baseline. Under this model, vendors complete one comprehensive assessment that satisfies multiple regulatory requirements—achieving "test once, comply many times" efficiency.
This approach significantly reduced workload for both the internal GRC team and vendor partners while maintaining full compliance coverage and audit readiness. The framework also simplified onboarding for new regulatory requirements, as mapping exercises identify existing controls that satisfy new obligations.
PAA: CXO Questions on Third-Party Cybersecurity Risk in the GCC
What is third-party cybersecurity risk?
Third-party cybersecurity risk refers to potential security threats introduced through external vendors, suppliers, contractors, and service providers who access enterprise systems, data, or networks. These risks emerge when organizations grant external entities permissions that attackers can exploit—either by directly compromising the vendor organization or by exploiting weak security controls in vendor-managed systems and applications that connect to enterprise infrastructure.
How can enterprises reduce vendor cyber risk in UAE & Saudi Arabia?
Enterprises reduce vendor cyber risk through structured frameworks combining initial risk tiering during vendor identification, tiered due diligence aligned with vendor criticality and data access levels, strong contractual protections including audit rights and breach notification requirements, and continuous monitoring throughout vendor relationships. Regional compliance with SAMA, NCA, and NESA provides regulatory alignment while zero-trust access controls limit potential damage from vendor compromises. Automation of assessment workflows accelerates onboarding while maintaining security rigor.
What are NCA and NESA requirements for vendors?
Saudi Arabia's NCA Essential Cybersecurity Controls (ECC) require organizations to conduct formal third-party risk assessments, ensure data localization for sensitive national information, and maintain documented evidence of vendor security controls and ongoing compliance. UAE's NESA Information Assurance Standards mandate similar controls including vendor audit capabilities, incident reporting protocols within specified timeframes, and security control verification for critical sector suppliers. Both frameworks emphasize continuous monitoring rather than point-in-time assessment.
How often should vendor cybersecurity assessments be done?
Assessment frequency should align with vendor risk tier classification. Critical vendors (Tier 1) warrant quarterly reviews and continuous external monitoring through automated rating platforms. High-risk vendors (Tier 2) require semi-annual assessments with evidence refresh. Lower-risk vendors (Tier 3) typically undergo annual recertification processes. Trigger events—security incidents, significant rating drops, organizational changes, or material business changes—should initiate immediate reassessment regardless of scheduled review cycles.
From Gatekeeper to Guardrail: Turning Vendor Risk into a Growth Enabler
Aligning Security, Procurement & Business Velocity
The traditional framing of third-party risk management positions security as a barrier to business objectives—an obstacle course that vendors and internal stakeholders must navigate before productive work can begin. Security teams slow down vendor onboarding with lengthy questionnaires. Compliance requirements create friction in procurement timelines. CISOs become the "Department of No," reactive blockers rather than strategic enablers.
This framing fundamentally misrepresents the value security provides—and creates organizational dysfunction that ultimately increases risk. Business units circumvent controls they perceive as obstacles to meeting legitimate objectives. Shadow IT proliferates as teams find workarounds. Risk actually increases precisely because security is positioned as an adversary rather than an enabler of safe business operations.
Progressive GCC enterprises reframe vendor risk management as a speed enabler rather than a speed limiter. Standardized, automated assessment processes actually accelerate compliant vendor onboarding compared to ad-hoc manual reviews that vary by assessor and lack consistent criteria. Pre-approved vendor pools eliminate repetitive evaluations for common service categories. Clear risk criteria and decision frameworks empower procurement teams to make confident decisions without constant security escalation that creates bottlenecks.
Building Digital Trust Across the GCC Supply Chain
Strong vendor risk management creates competitive differentiation in GCC markets beyond mere compliance satisfaction. Enterprises demonstrating mature security practices attract better vendor partners—organizations that value working with clients who understand and respect security requirements, maintain professional assessment processes, and offer stable long-term relationships built on mutual trust.
These relationships prove more resilient during incidents and more responsive to emerging threats. Vendors who have invested in building trust with security-mature clients prioritize those relationships when incidents require rapid communication and coordinated response. The relationship becomes collaborative rather than adversarial.
For organizations serving government clients or operating in regulated sectors, documented vendor risk management programs satisfy procurement requirements that competitors without such programs simply cannot meet. Security maturity becomes a market access enabler rather than merely a compliance obligation—a genuine competitive advantage in bidding for sensitive contracts.
VLink's cybersecurity consulting services support GCC enterprises in building these differentiated capabilities—transforming vendor risk from liability to strategic advantage through structured program development and implementation.
CXO Action Checklist: Getting Started in the Next 90 Days
Immediate (0–30 Days)
- Conduct complete vendor inventory audit—identify all third-party relationships including shadow IT applications discovered through CASB, network analysis, and business unit surveys
- Classify vendors into risk tiers (Critical, High, Medium, Low) based on data access levels, system integration depth, and operational criticality to business functions
- Review existing contracts for Tier 1 vendors—identify gaps in security clauses, audit rights, breach notification requirements, and data sovereignty provisions
- Establish baseline external security ratings for critical vendors using automated scanning platforms to enable trend monitoring
- Brief executive leadership and board risk committees on current vendor risk posture and planned remediation approach
Short-Term (30–60 Days)
- Develop standardized vendor security questionnaires aligned with NCA, NESA, and SAMA requirements as applicable to organizational sector
- Implement tiered due diligence workflows—define "Lite" versus "Deep Dive" assessment criteria and resource allocation models
- Create contract amendment templates incorporating essential security provisions for renegotiation of existing vendor relationships
- Establish cross-functional vendor risk committee with representatives from Security, Procurement, Legal, Finance, and key Business Units
- Define escalation procedures and decision rights for vendor risk exceptions and expedited onboarding requests
Strategic (60–90 Days)
- Implement continuous monitoring program with automated alerts for vendor security posture changes and trigger event detection
- Deploy Unified Control Framework mapping overlapping regulatory requirements (ISO 27001, NCA ECC, NESA IAS, SAMA CSF)
- Develop board-level vendor risk reporting dashboard with KPIs aligned to business objectives and regulatory requirements
- Evaluate automation opportunities for vendor onboarding, assessment workflows, and evidence collection processes
- Establish vendor risk program maturity targets and improvement roadmap for the following 12-month period
Conclusion
Third-party vendor risk has evolved from operational concern to strategic imperative for GCC enterprises operating in an increasingly interconnected threat environment. The organizations succeeding in this environment treat vendor onboarding not as a compliance checkbox to complete but as a deliberate architecture of trust—one that enables business velocity while maintaining security integrity across complex vendor ecosystems.
The frameworks, approaches, and action steps outlined in this playbook provide CXOs with practical pathways forward regardless of current program maturity. Whether implementing tiered due diligence workflows, deploying zero-trust access controls for third-party interactions, or building unified compliance frameworks that reduce audit fatigue, the objective remains consistent: transforming vendor relationships from risk liabilities into resilient partnerships that support organizational growth across UAE, Saudi Arabia, and the broader GCC region.
The next 90 days present an opportunity to establish foundations that will define vendor security postures for years ahead. The enterprises acting decisively today will find themselves positioned to capitalize on regional digital transformation initiatives, government smart city programs, and expanding cloud adoption—while competitors remain constrained by outdated, manual approaches to third-party risk that create bottlenecks and blind spots.










 Shivisha Patel
Shivisha Patel

















