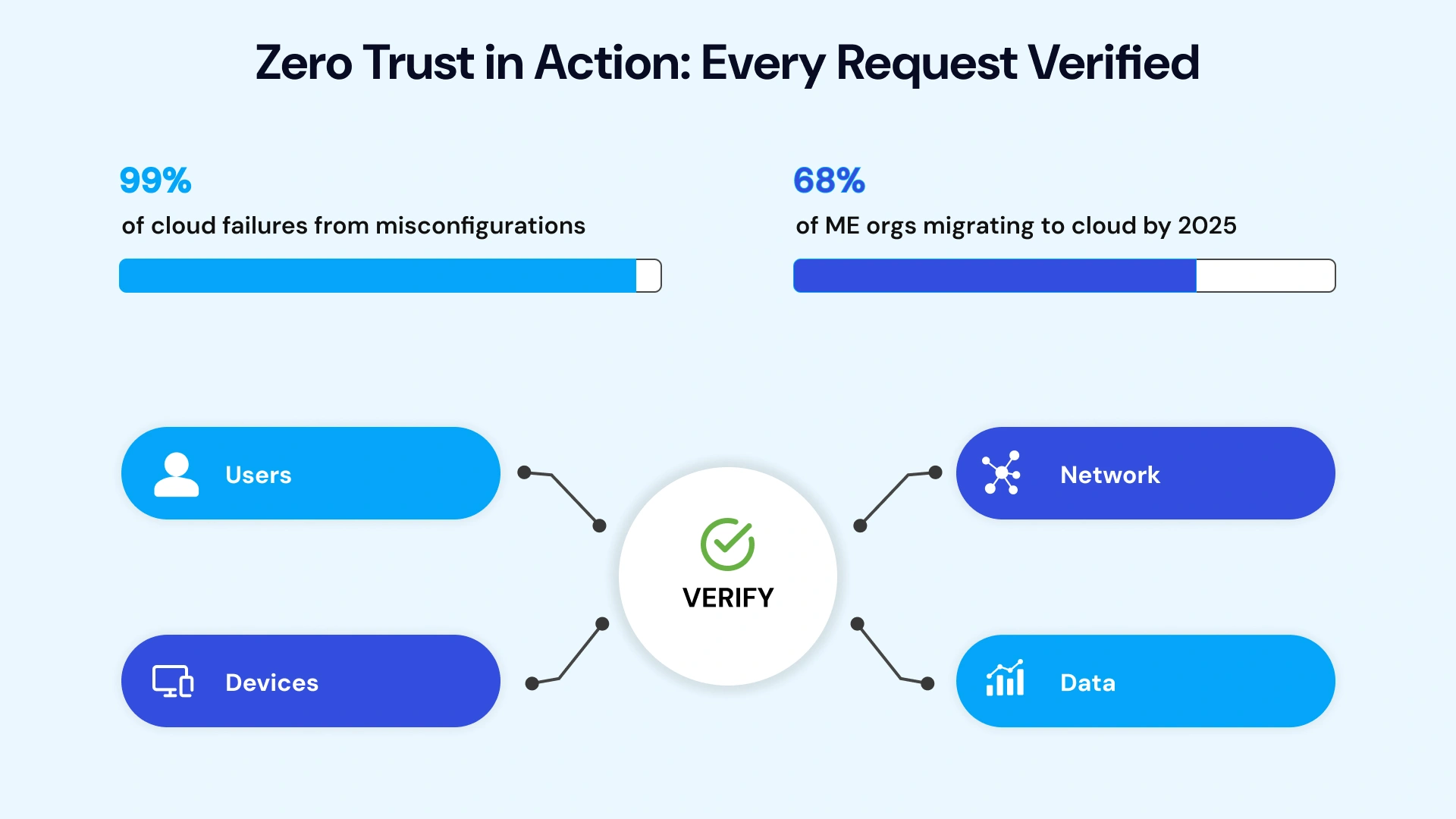
The Gulf Cooperation Council is racing toward a digital-first future. Vision 2030 initiatives across Saudi Arabia, the UAE, Qatar, and Oman are driving unprecedented cloud adoption, with 68% of Middle Eastern organizations planning to migrate majority operations to the cloud by mid-2025.
Yet beneath this transformation lies an uncomfortable truth: cybersecurity strategies remain anchored to legacy, perimeter-based models built for an era of on-premises infrastructure.
The numbers tell the story. The GCC cloud security market is projected to surge from $3.38 billion in 2024 to $14.39 billion by 2031—a 23% CAGR that signals both opportunity and urgency. Cyberattacks targeting regional organizations have increased 20-25% year over year. And here's the critical insight: 99% of cloud security failures through 2025 are predicted to stem from customer misconfigurations, not external breaches.
This isn't a technology gap. It's a strategic one. And for enterprises that recognize cloud-native cybersecurity as a competitive accelerator rather than a cost center, the Gulf presents one of the world's most underserved—and lucrative—markets.
Why Cloud-Native Cybersecurity Is the Gulf's Next Competitive Advantage
The Gulf's digital ambitions are not subtle. Saudi Arabia's NEOM project alone encompasses smart cities requiring millions of IoT endpoints. The UAE's data center capacity is projected to reach 5-6 GW by 2030, driven primarily by AI workloads. Qatar's financial sector is undergoing rapid digitization ahead of continued economic diversification.
This infrastructure explosion creates an exponentially expanding attack surface. Traditional security architectures—designed for static, centralized environments—cannot scale to protect distributed microservices, ephemeral containers, and API-first applications.
Consider a regional bank launching a digital-only subsidiary to compete with fintechs. The speed demanded by DevOps pipelines clashes directly with manual security reviews built for quarterly release cycles. The bank faces a binary choice: slow down innovation or accept unquantified risk.
Cloud-native cybersecurity dissolves this false dichotomy. By embedding security into the development lifecycle and automating policy enforcement across distributed environments, enterprises can maintain both velocity and protection.
The competitive advantage compounds over time. Organizations that master cloud-native security can launch digital services faster, satisfy regulatory audits with automated compliance reporting, and reduce breach probability through continuous posture management. Those clinging to legacy models will find themselves perpetually reactive, patching vulnerabilities after they've been exploited.
What Cloud-Native Cybersecurity Actually Means (CXO-Friendly Overview)
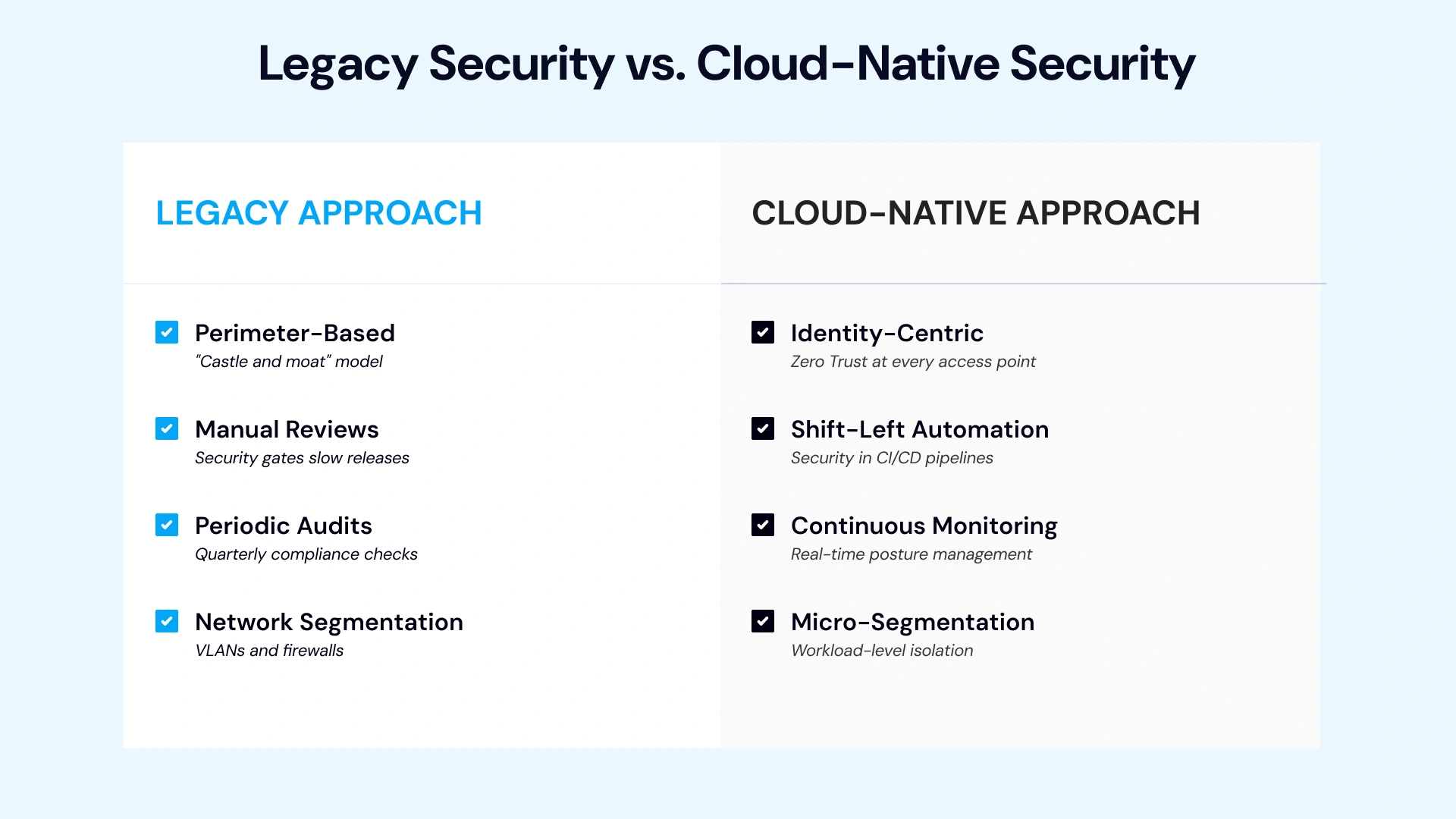
Cloud-native cybersecurity represents a fundamental architectural shift, not merely a vendor swap. Understanding this distinction is essential for executives evaluating security investments.
From Perimeter Defense to Identity-, Service-, and API-Level Security
Traditional security assumed a clear boundary: inside the firewall was trusted, outside was hostile. Cloud-native environments eliminate this boundary entirely. Workloads spin up across multiple regions, services communicate through APIs, and identities—both human and machine—become the actual perimeter.
Zero Trust architecture operationalizes this reality. Every request is authenticated, authorized, and encrypted regardless of origin. Identity becomes the control plane, with Cloud Infrastructure Entitlement Management (CIEM) enforcing least-privilege access automatically across AWS, Azure, and GCP environments.
Shift-Left Security & DevSecOps Integration
Shift-left security moves vulnerability detection from post-deployment remediation to pre-deployment prevention. Security scanning integrates directly into CI/CD pipelines—developers cannot commit code containing hardcoded credentials or critical vulnerabilities.
Infrastructure as Code (IaC) scanning extends this principle to cloud configurations. Misconfigurations—the root cause of most cloud breaches—are caught before resources are provisioned, not discovered during incident response.
Continuous, Autonomous Detection Across Distributed Environments
Cloud-native security operates continuously, not periodically. Cloud Security Posture Management (CSPM) tools monitor configurations in real-time, alerting on drift from compliance baselines. Cloud Workload Protection Platforms (CWPP) secure containers and serverless functions throughout their lifecycle.
The goal is autonomous response at machine speed. When a misconfigured storage bucket is detected, remediation happens in seconds—not days waiting for change approval boards.
The Gulf Market Gap - Why Cloud-Native Cybersecurity Remains Underserved
The opportunity in Gulf cloud-native cybersecurity stems from a measurable maturity gap. Regional content predominantly focuses on data protection regulations like PDPL or general cloud security concepts—very little addresses cloud-native architectural approaches.
Market Signal 1 — Cloud Adoption Outpaces Cyber Maturity
GCC enterprises are adopting cloud at global-leading rates, yet security capabilities lag 18-24 months behind infrastructure investments. The UAE cloud security market alone is projected to reach $2.1 billion by 2030, but current spending skews heavily toward legacy tools retrofitted for cloud environments.
This creates a specific vulnerability pattern: organizations running containerized workloads protected only by virtual firewalls, or API-driven architectures without runtime protection. The attack surface has evolved; the defense hasn't.
Market Signal 2 — Sector-Specific Gaps (Banking, Oil & Gas, Telco)
Each sector demands specialized cloud-native security implementations, yet vendor offerings remain largely horizontal. The localization gap—adapting global tools to regional compliance and operational requirements—remains wide open.
Market Signal 3 — Regulatory Evolution (KSA PDPL, UAE NESA, Qatar QCB)
Manual compliance mapping consumes 30-40% of security team capacity. Organizations that implement automated compliance-as-code will redirect those resources toward strategic initiatives while reducing audit risk.
| Gap Area | Current State | Cloud-Native Solution |
| Container Security | Virtual firewalls only | Runtime protection + image scanning |
| API Protection | Perimeter WAF | API gateway + behavioral analysis |
| Compliance | Manual quarterly audits | Automated continuous compliance |
| IAM | Static role assignments | CIEM with least-privilege automation |
Architecture Overview - What a Cloud-Native Security Stack Looks Like
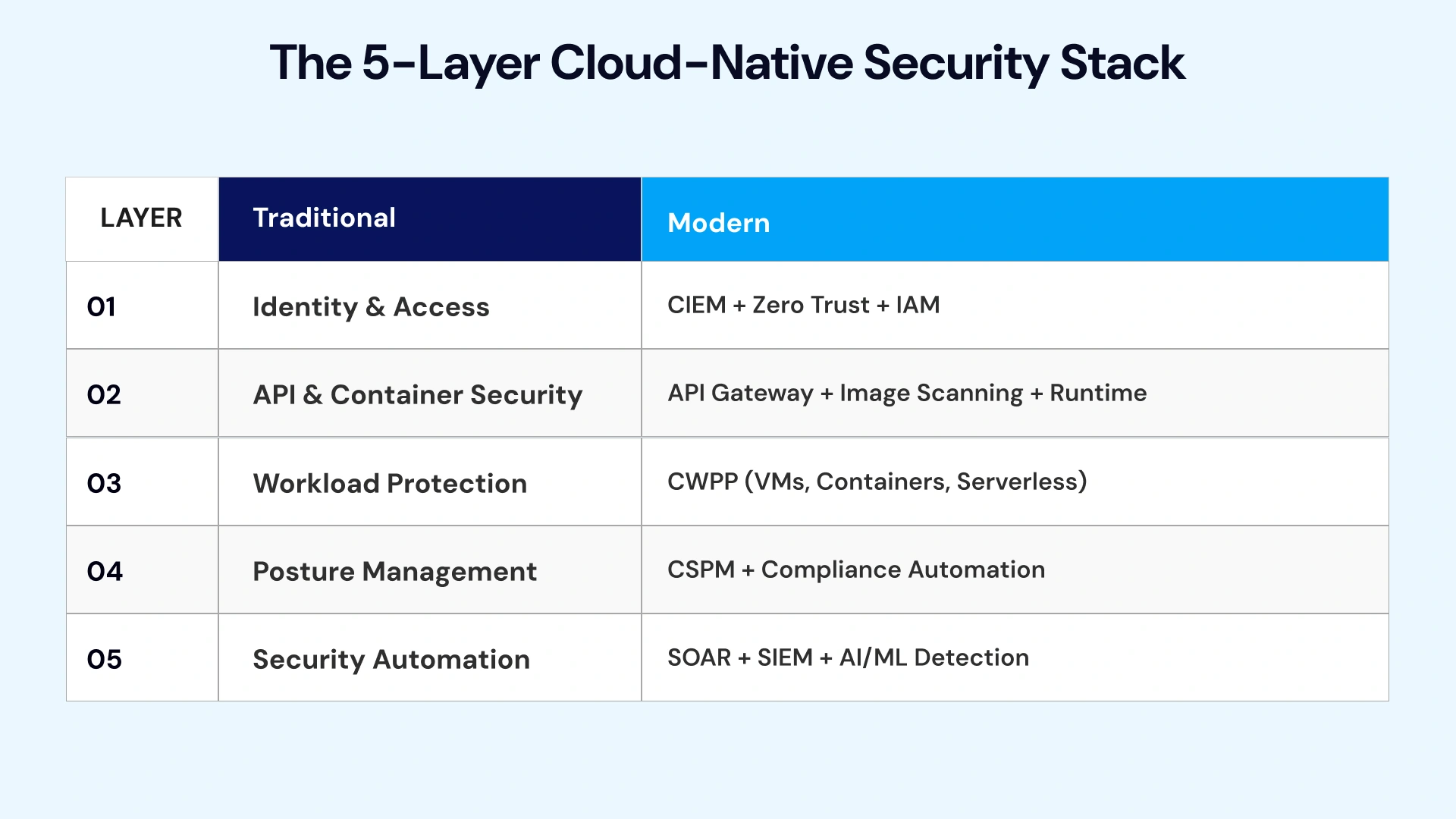
Cloud-native security operates as a layered fabric, with each layer addressing specific threat vectors while integrating with adjacent controls. Understanding this architecture enables informed vendor evaluation and implementation planning.
Layer 1 — Identity & Access (Zero Trust Foundations)
Identity forms the foundational layer. Cloud Infrastructure Entitlement Management (CIEM) platforms discover all human and machine identities across cloud environments, analyze entitlements against actual usage, and automatically remediate excessive permissions.
For Gulf enterprises managing multiple cloud providers—AWS in Dubai, Azure in Riyadh, private cloud in Doha—unified identity governance becomes essential. Fragmented IAM creates the permission sprawl that attackers exploit.
Layer 2 — API, Microservices, and Container Security
APIs are the connective tissue of cloud-native applications—and the primary attack vector. API security platforms provide discovery, runtime protection, and abuse detection for the thousands of APIs that modern applications expose.
Container security addresses the unique challenges of ephemeral workloads. Image scanning catches vulnerabilities before deployment. Runtime protection detects anomalous behavior during execution. Kubernetes-native policies enforce segmentation between pods.
Layer 3 — Cloud Workload Protection (CWPP)
Cloud Workload Protection Platforms secure compute regardless of form factor—virtual machines, containers, serverless functions. CWPP combines vulnerability management, behavioral monitoring, and exploit prevention into a unified agent.
The value proposition for Gulf enterprises is consistency. A single platform protecting workloads across AWS Middle East, Oracle Jeddah, and on-premises data centers eliminates the visibility gaps that attackers target.
Layer 4 — Cloud Security Posture Management (CSPM)
CSPM continuously monitors cloud configurations against security baselines and compliance frameworks. When a storage bucket is accidentally made public or a security group allows unrestricted SSH access, CSPM detects and alerts—or automatically remediates—within minutes.
Layer 5 — Security Automation & Event Correlation (SOAR + SIEM + AI)
The orchestration layer integrates signals from all security tools into unified detection and response. Security Information and Event Management (SIEM) aggregates logs. Security Orchestration, Automation and Response (SOAR) automate playbook execution. AI models identify attack patterns that rule-based systems miss.
The talent shortage in Gulf cybersecurity—a recognized constraint across the region—makes automation essential. Organizations cannot hire enough analysts to manually investigate every alert. Machine-speed response becomes the only scalable approach.
The Business Case - Why Cloud-Native Cybersecurity Unlocks Enterprise Value
Security investment decisions require business justification. Cloud-native cybersecurity delivers measurable returns across three dimensions that resonate with board-level stakeholders.
Faster Time-to-Market for Digital Services (Shift-Left + Automation)
Organizations implementing DevSecOps report deployment cycles measured in hours rather than weeks. A UAE digital bank reduced release timelines from 14 days to 4 hours by integrating security scanning into CI/CD pipelines—eliminating the bottleneck of manual security reviews while maintaining regulatory compliance.
The acceleration compounds strategically. Faster releases enable more frequent experimentation, faster customer feedback loops, and ultimately better products. Security becomes an innovation enabler rather than a gate.
Reduced Breach Probability & Costs (CSPM + Real-Time Detection)
Cloud misconfiguration remains the leading cause of breaches, and the costs are substantial. Regional enterprises face both direct remediation expenses and regulatory penalties that can reach millions of dirhams under evolving GCC frameworks.
CSPM platforms eliminate the configuration drift that creates vulnerability windows. Continuous monitoring catches issues before attackers discover them. The ROI calculation is straightforward: prevention costs a fraction of incident response.
Better Audit Readiness for PDPL, NESA, SAMA, QCB
Compliance teams at Gulf enterprises spend enormous effort preparing for audits—gathering evidence, documenting controls, demonstrating remediation. Cloud-native security tools automate this burden.
Dashboard reporting mapped to specific SAMA or NESA controls provides real-time board visibility. Audit preparation shifts from quarterly fire drills to continuous demonstration. The freed capacity can focus on strategic security improvements rather than evidence collection.
Strategic Framework - The Gulf CXO's Cloud-Native Security Playbook
Transforming security architecture requires structured execution. The following framework provides a decision-making methodology for Gulf executives building cloud-native security capabilities.
Step 1 — Assess Cloud Security Maturity (People, Tools, Workloads)
Begin with honest capability assessment across three dimensions. People: Do existing teams possess cloud-native security skills, or is the organization dependent on legacy expertise? Tools: Are current security investments designed for cloud environments, or retrofitted perimeter tools? Workloads: What percentage of infrastructure runs containerized, serverless, or multi-cloud deployments?
This assessment reveals the maturity gap specific to your organization and prioritizes investment areas.
Step 2 — Identify High-Risk Workloads for Containerization
Not all workloads require cloud-native security immediately. Prioritize based on risk exposure: customer-facing applications, financial transaction systems, and workloads processing regulated data demand immediate attention. Internal tools with limited data access can follow.
Step 3 — Build a Unified Policy Fabric Across Clouds
Multi-cloud environments require consistent policy enforcement. Establish governance frameworks that apply uniformly across AWS, Azure, GCP, and private cloud deployments. Compliance-as-code ensures that regional requirements—like data residency restrictions—are automatically enforced regardless of deployment target.
Step 4 — Integrate DevSecOps into CI/CD Pipelines
Shift-left security requires tooling integration. Embed vulnerability scanning, secrets detection, and IaC security into existing development workflows. The goal is friction-free security—developers receive immediate feedback without context-switching to separate tools.
Step 5 — Automate Monitoring, Response, and Governance
The final phase establishes autonomous security operations. CSPM monitors configurations continuously. SOAR playbooks execute response procedures automatically. AI models surface threats that manual analysis would miss. Human analysts focus on strategic decisions rather than alert triage.
| High Impact / Low Complexity | High Impact / High Complexity |
| CSPM implementation, IAM modernization, Basic SIEM deployment | Full API security platform, Container runtime protection, CNAPP deployment |
| Low Impact / Low Complexity | Low Impact / High Complexity |
| Basic network segmentation, Logging standardization | Full SOAR before SOC maturity, Zero Trust without identity foundation |
Answering the Most Searched Questions
1. Why is cloud-native cybersecurity critical for the Gulf's digital economy?
The Gulf's Vision 2030 initiatives depend on cloud infrastructure for smart cities, digital government services, and financial innovation. Traditional perimeter security cannot protect distributed microservices, APIs, and containerized workloads. Cloud-native cybersecurity enables the agility these initiatives require while maintaining the security posture that regulators demand.
2. What are the differences between cloud-native security and traditional cloud security?
Traditional cloud security applies perimeter-based controls—firewalls, VPNs, network segmentation—to cloud environments. Cloud-native security is architecturally different: identity-centric rather than network-centric, integrated into development pipelines, automated rather than manual, and designed for ephemeral, distributed workloads from the ground up.
3. How can Gulf enterprises secure microservices, containers, and APIs?
Securing modern architectures requires layered controls: container image scanning before deployment, runtime protection during execution, API gateways with behavioral analysis, and service mesh encryption for inter-service communication. Cloud-Native Application Protection Platforms (CNAPP) consolidate these capabilities into unified solutions.
4. What are the best cloud-native security tools for Gulf enterprises?
Tool selection depends on specific requirements, but Gulf enterprises should prioritize platforms offering: in-region data residency options, pre-built compliance mappings for SAMA/NESA/PDPL, multi-cloud support covering AWS Middle East, Azure UAE, and Oracle Jeddah, and integration with regional managed security service providers.
5. How does Zero Trust fit into cloud-native security for GCC organizations?
Zero Trust is the architectural foundation of cloud-native security. In environments where workloads span multiple clouds and data centers, network location cannot determine trust. Identity verification for every request—human and machine—becomes the control plane. GCC organizations implement Zero Trust through CIEM platforms, micro-segmentation, and continuous authentication.
Real-World Examples - How Early Adopters Are Leading
Case Example — Saudi Fintech Scaling Secure Kubernetes
A Saudi-based fintech scaling its payment processing platform faced a critical challenge: rapid Kubernetes adoption had outpaced security controls. The organization implemented a CNAPP solution providing automated container scanning, runtime protection, and compliance mapping to SAMA requirements.
Results included 100% visibility across containerized workloads, automated compliance reporting reducing audit preparation by 60%, and zero security-related deployment delays.
Case Example — UAE Telecom Improving API Security Posture
A major UAE telecom launching 5G services discovered over 3,000 APIs across its infrastructure—far more than documented. An API security platform provided discovery, classification, and runtime protection, identifying shadow APIs and preventing credential stuffing attacks targeting customer portals.
Case Example — Oman Energy Sector Using IaC Security for Infrastructure
An Omani energy company migrating critical infrastructure to cloud required Infrastructure as Code security to prevent misconfigurations that could expose operational technology systems. IaC scanning integrated into Terraform pipelines blocked 47 high-risk configurations in the first month, including storage buckets that would have been publicly accessible.
Roadmap - How Gulf Enterprises Can Begin Their Cloud-Native Security Journey
Transformation begins with practical first steps. Gulf enterprises initiating cloud-native security journeys should consider the following roadmap.
First, build a cross-functional cloud security guild. Bring together security, platform engineering, and application development teams to establish shared ownership. Cloud-native security cannot succeed as a siloed function.
Second, adopt a unified tooling approach. Vendor sprawl creates visibility gaps and operational complexity. Consolidate toward platforms that address multiple cloud-native security domains rather than point solutions for each capability.
Third, start with visibility, posture management, and identity hardening. These foundational capabilities deliver immediate value while enabling more advanced implementations. CSPM deployment typically provides the fastest time-to-value for organizations beginning their journey.
Fourth, run a cloud-native security pilot for one business unit. Select a digital-first team or application with executive sponsorship. Demonstrate success at limited scope before enterprise-wide rollout.
Organizations seeking guidance on cloud-native security implementations can explore VLink's Cloud Consulting Services and Cybersecurity Services for expert support tailored to GCC requirements.
Conclusion - The Gulf's Cloud-Native Security Window Won't Stay Underserved for Long
The Gulf's cloud-native cybersecurity gap represents both risk and opportunity. Organizations that continue securing modern architectures with legacy approaches will face mounting breach probability, compliance penalties, and competitive disadvantage.
But for enterprises that recognize this moment, the opportunity is substantial. GCC organizations can leapfrog global markets by embracing cloud-native security architectures aligned with regional sovereignty requirements and regulatory frameworks.
The market will mature. Vendors will localize. Competition will intensify. The enterprises that act now—building cloud-native security capabilities while the gap remains underserved—will establish durable competitive advantages.
The question isn't whether Gulf enterprises will adopt cloud-native cybersecurity. It's whether they'll lead the transformation or follow it.











 Shivisha Patel
Shivisha Patel

















