In today's digital age, cyber threats are constantly evolving, posing a significant risk to businesses of all sizes. Traditional security measures often struggle to keep pace with these sophisticated attacks. This is where Machine Learning (ML) in Cybersecurity emerges as a game-changer. By leveraging the power of ML, organizations can proactively identify and respond to threats, enhancing their overall security posture
Machine learning (ML) is a type of artificial intelligence (AI) that allows systems to learn and improve from data without being explicitly programmed. In cybersecurity, ML algorithms can analyze vast amounts of data to identify patterns and anomalies that might indicate a security threat. This enables businesses to defend themselves against cyberattacks and minimize potential damage proactively.
As a business CXO, you are fully responsible for the security of your organization's data and systems. A cyberattack can mainly disrupt operations, damage your reputation, and result in financial losses significantly. ML in cyber security offers an ideal & powerful tool to strengthen your security posture and protect your business from these threats.
Here are some compelling statistics that highlight the importance of how machine learning is used in cybersecurity.
These statistics show that more businesses are embracing machine learning in cybersecurity. Implementing ML-driven solutions will give such companies a significant advantage in the fight against cybercrime.
In this blog, we will explore how machine learning works in cybersecurity, but let's first understand the core concepts and types of machine learning.
Machine Learning in Cybersecurity: Concepts and Types
Machine learning, a subset of Artificial Intelligence (AI), empowers computers to learn and improve from experience without explicit programming. In the context of cybersecurity services, ML algorithms analyze vast datasets to identify patterns, anomalies, and threats that traditional security measures might miss.
Here's a breakdown of key concepts and types of machine learning relevant to cybersecurity:
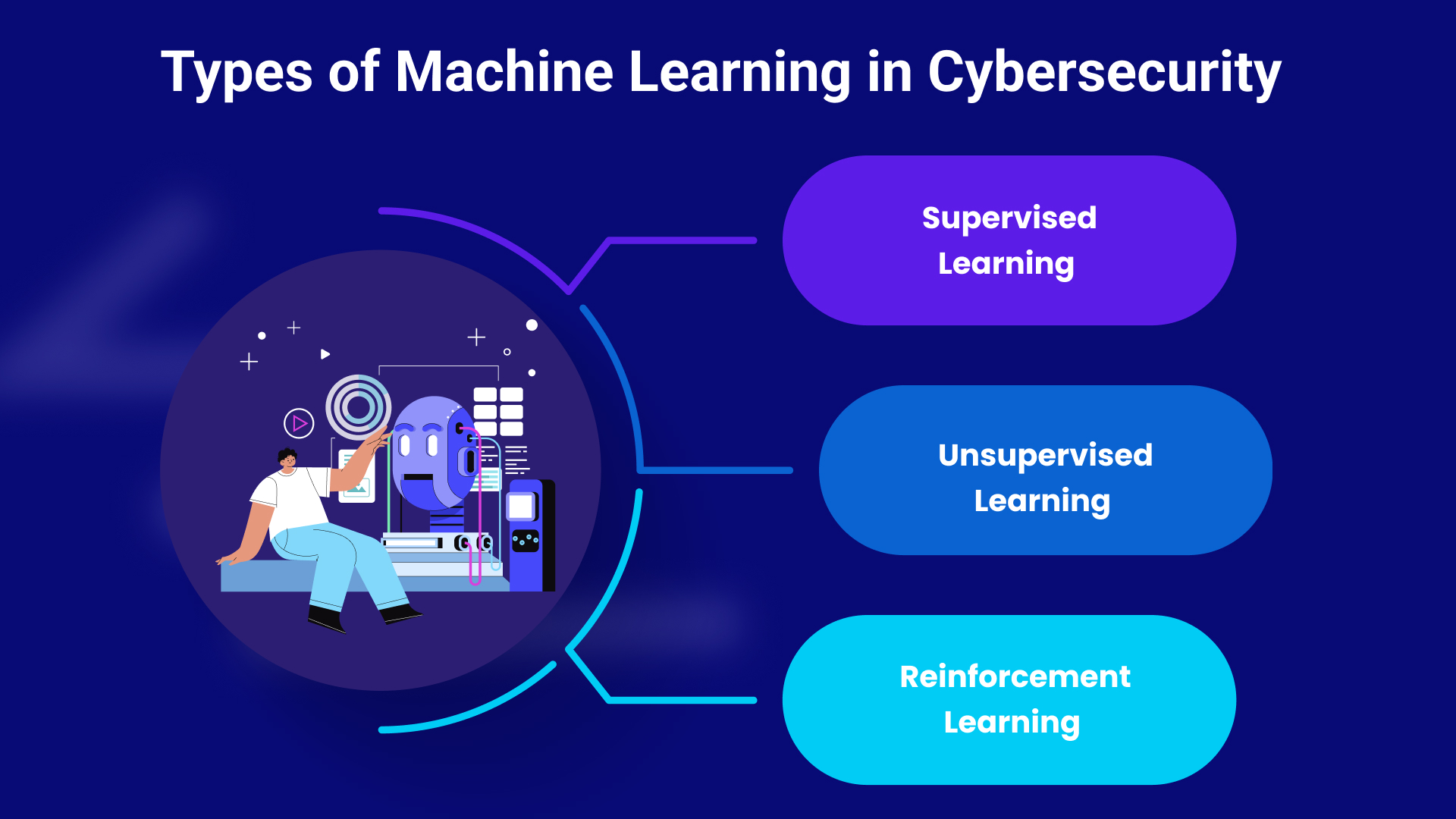
1. Supervised Learning: Learning from Labeled Examples
Concept: Imagine training a dog to recognize the command "sit." You provide the dog with examples (input) and the desired outcome (output) – "sit" command followed by the dog sitting down. Supervised learning works similarly. This type of machine learning cybersecurity effectively classifies data as harmful or benign and detects threats such as denial-of-service attacks.
- Concept: Imagine training a dog to recognize the command "sit." You provide the dog with examples (input) and the desired outcome (output) – "sit" command followed by the dog sitting down. Supervised learning works similarly. This type of machine learning in cybersecurity effectively classifies data as harmful or benign and detects threats such as denial-of-service attacks.
Cybersecurity Applications:
- Malware Classification: Train models to classify files as either malicious or benign. The exact types here would be viruses and ransomware. Basic features used include file size or type and code behavior.
- Phishing Detection: These are methods for identifying phishing emails using sender addresses, subjects, links, or attachments.
- Intrusion Detection: Network traffic is analyzed and classified into either normal or hostile behavior based on an analysis of specific characteristics and anomalies.
2. Unsupervised Learning: Discovering Hidden Patterns
- Concept: Unlike supervised learning, unsupervised learning is a type of ML in cyber security that deals with unlabeled data. The algorithm explores data to discover hidden patterns, structures, and relationships.
Cybersecurity Applications:
- Anomaly Detection: Identifying different forms of abnormal activity on the network, such as spikes in traffic, various forms of login attempts, or abnormal actions of users. This machine-learning cybersecurity helps find insider threats, zero-day attacks, and other unknown threats.
- User Behavior Analysis: The study focuses on users' behavior that does not seem normal, such as excessive file downloading, strange login times, or access to sensitive information after everyday duty has ended.
- Network Segmentation: Machine learning cybersecurity systems would be segmented based on their network behavior, followed by the identification of potential vulnerabilities within those specific segments.
3. Reinforcement Learning: Learning Through Rewards and Penalties
- Concept: This type of ML in cyber security learning involves an agent who learns to interact with an environment by performing actions and receiving rewards or penalties based on the outcomes.
Cybersecurity Applications:
- Developing AI-powered security agents: Learning how these agents can be programmed to defend systems through interaction with simulated attack scenarios, where successful defenses are rewarded and failures are penalized. This can lead to stronger, more challenging, and more adaptive systems.
- Optimizing Security Configurations: One ideal ML application of reinforcement learning is optimizing security configurations, such as firewall rules, intrusion detection system thresholds, and access control policies.
By understanding these core concepts and the various types of machine learning, organizations can effectively leverage ML in cyber security posture and stay ahead of the evolving threat landscape.
Now, let’s explore how machine learning in cyber security works effectively in detail.
How Machine Learning Works in Cybersecurity
Imagine a cybersecurity team sifting through terabytes of data from firewalls, intrusion detection systems, and endpoint security solutions. It's like trying to find a needle in a haystack but with exponentially more hay and needles! This is where machine learning (ML) becomes an invaluable ally.
ML in cyber security empowers security teams to automate the analysis of this massive data deluge, identifying subtle patterns and anomalies that human analysts might miss. Here's a deeper look at how it works:
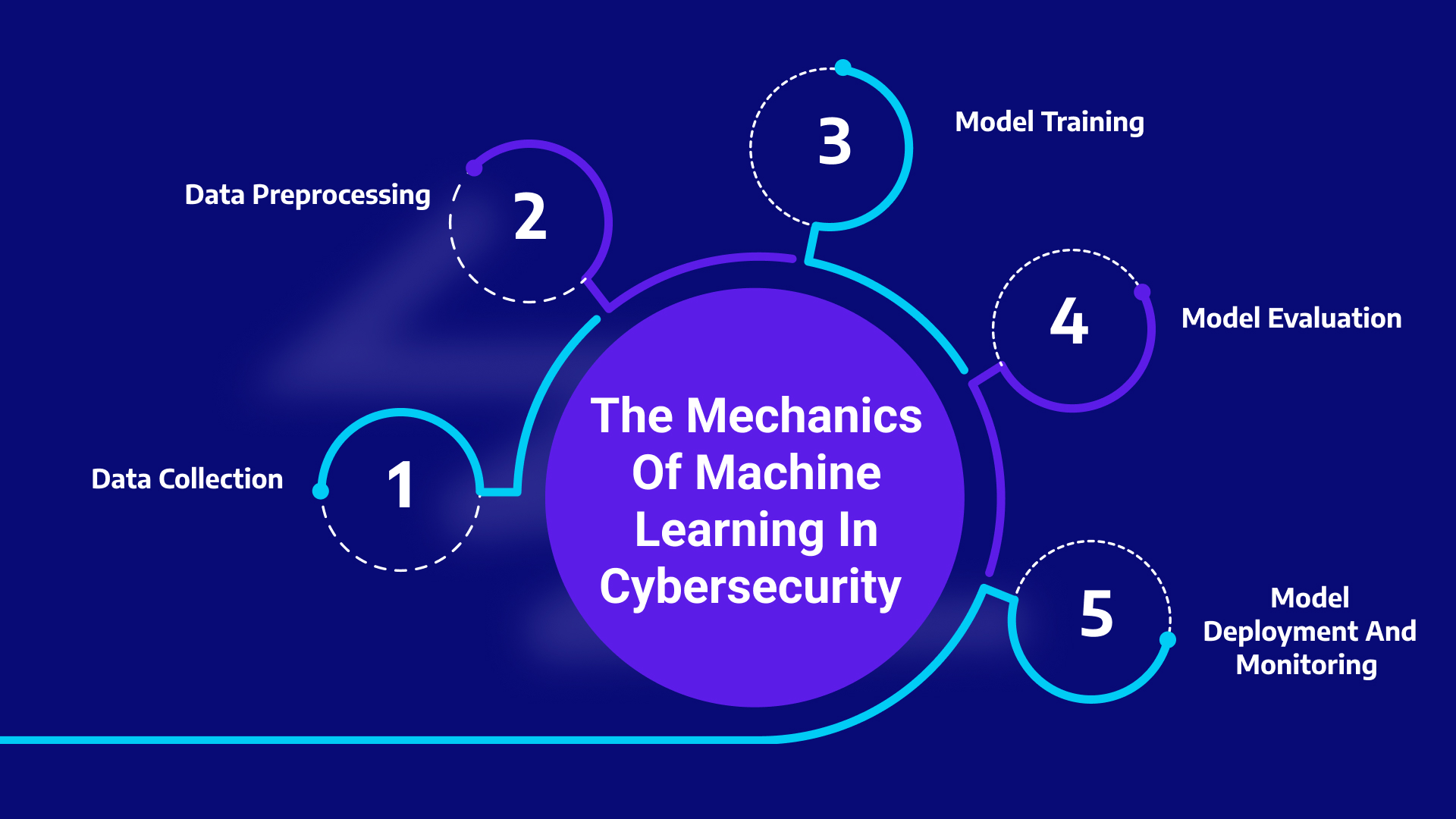
1. Data Collection: The Foundation of Intelligence
The first step is to collect relevant data from various sources, such as network traffic logs, system logs, user activity data, and security events. This includes:-
Data Sources: ML thrives on data. Cybersecurity teams gather data from a variety of sources, including:
- Network Traffic Logs: Capturing all network communication, including inbound and outbound traffic, protocols used, and source/destination addresses.
- System Logs: Recording events and activities occurring within operating machine learning cybersecurity systems, ML applications, and network devices.
- Security Event Logs: Collecting alerts and notifications from security tools like firewalls, intrusion detection systems, and antivirus software.
- User Activity Data: Monitoring user logins, file access patterns, and other user behaviors.
- Threat Intelligence Feeds: Integrating external threat intelligence data from reputable sources to enrich internal datasets.
Data Volume and Velocity: The volume of data generated is immense and constantly growing. ML algorithms are designed to handle this scale effectively, processing data in real-time to provide immediate insights.
2. Data Preprocessing: Preparing Data for Consumption
The collected data is then cleaned, formatted, and transformed into a usable format for the ML algorithms. Raw data is often messy and unstructured. Before it can be fed to ML algorithms, it needs to be preprocessed:
Data Cleaning: Removing duplicates, handling missing values, and correcting inconsistencies.
Data Transformation: Converting data into a suitable format for ML algorithms. This may involve:
- Feature Engineering: Creating new features from existing data to improve model accuracy.
- Normalization/Standardization: Scaling data to a typical range to prevent certain features from dominating the learning process.
- Dimensionality Reduction: Reducing the number of features to improve model performance and reduce computational complexity.
3. Model Training: Teaching the Machine to Recognize Threats
Now, the chosen AI/ML model is trained on the prepared data. During training, the model learns to identify patterns and relationships within the data. This includes:-
Algorithm Selection: Choosing the appropriate ML algorithm depends on the specific cybersecurity use case. Common choices include:
Supervised Learning:
- Classification: Classifying network traffic as malicious or benign, identifying phishing emails, and categorizing malware families.
- Regression: Predicting the likelihood of a security incident.
Unsupervised Learning:
- Anomaly Detection: Identifying unusual network activity, detecting malicious insiders, and discovering unknown threats.
- Clustering: Grouping similar network events or user activities to identify potential cybersecurity threats.
Training Process: The selected algorithm is trained on a labeled dataset (supervised learning) or an unlabeled dataset (unsupervised learning). During training, the model learns to identify patterns, relationships, and anomalies within the data.
4. Model Evaluation: Assessing Performance and Accuracy
Once trained, the model is evaluated on a separate dataset to assess its accuracy and effectiveness in detecting threats. This includes:-
Validation Sets: Trained models are evaluated on a separate dataset (validation set) to assess their performance. Key metrics include:
- Accuracy: The proportion of correctly classified instances.
- Precision: The proportion of true positives among all optimistic predictions.
- Recall: The proportion of true positives identified out of all actual positives.
- False Positive Rate: The proportion of false positives among all negative instances.
Fine-tuning: Based on the evaluation results, the model may be fine-tuned by adjusting parameters, adding more data, or modifying the training process.
5. Model Deployment and Monitoring: Real-Time Threat Detection
Now, if the model performs well, it's time to deploy it into production to analyze live data and identify security threats. This includes:-
- Integration: Once evaluated and refined, the trained model is integrated into the organization's security infrastructure.
- Real-time Analysis: The model continuously analyzes incoming data streams (network traffic, security logs, etc.) to identify potential threats.
- Alerting and Response: When the model detects a potential threat, it triggers alerts and notifications to security teams.
- Continuous Monitoring: The model's performance is continuously monitored and evaluated to ensure it remains effective against evolving threats. Regular retraining and updates are essential to maintaining accuracy and addressing new threats.
Key Considerations:
- Explainability: Understanding how and why an ML model makes certain decisions is crucial for building trust and ensuring compliance.
- Bias and Fairness: Ensuring that ML models are unbiased and do not discriminate against specific users or groups.
- Transparency: Maintaining transparency in the use of ML in cybersecurity to build trust with customers and stakeholders.
By following these steps and addressing the key considerations, organizations can effectively leverage machine learning cybersecurity posture and stay ahead of the ever-evolving threat landscape.
Next, let's explore the key benefits and challenges that organizations face when adopting ML cybersecurity solutions.
Top 10 Benefits of Machine Learning in Cybersecurity
Machine learning is boundless when it comes to its cybersecurity benefits. Here is the list of machine learning uses benefits in cybersecurity:
1. Detection Improvement: One of the exclusive features of ML in cyber security is its capability to analyze large amounts of data and recognize minimal patterns or peculiarities in the input that traditional security systems are likely to miss. Thus, it is much earlier to detect a threat, and it leads to responding more rapidly.
2. Improved Accuracy: In ML cybersecurity, machine learning models can keep learning forever and improve accuracy in terms of threat detection, thus resulting in fewer false positives.
3. Proactive Security: A business can predict potential threats that will undoubtedly occur with ML cybersecurity and take proactive steps to counter them.
4. Automated Threat Analysis: ML automates most of the processes and repetitive tasks associated with threat analysis. This condition allows security personnel to focus on more complex issues.
5. Scalability: Machine learning in cyber security works effectively even when given a lot of data generated by modern networks and security devices, enabling organizations to maintain a security posture.
6. Reduced Response Times: In many security incidents, machine learning has automated detection and analysis of the threat to respond rapidly to a security incident.
7. Cost Savings: Automation of security tasks and the reduced necessity of human intervention will result in considerable cost savings for companies in ML cybersecurity.
8. Improved Incident Response: ML-based information and Event Management (SIEM) can produce solid insight into an incident in real-time, enabling a fast, effective, and efficient response.
9. Better Protection Against Zero-Day Threats: ML in cyber security can help identify and mitigate zero-day threats, which are new attacks for which there are no existing defenses.
10 . Enhanced Compliance: Machine learning in cyber security assists organizations in complying with security regulations and industry standards.
Challenges of Implementing ML in Cybersecurity
While machine learning offers significant advantages in enhancing cybersecurity, several challenges must be addressed for successful implementation. Such as:-
Data-Related Challenges:
- Data Quality and Availability: High-quality, diverse, and sufficient training data is crucial for effective ML models. Insufficient or low-quality data can lead to inaccurate predictions and unreliable results.
- Data Bias: Biases present in the training data can be reflected in the model, leading to biased outcomes and potentially discriminatory decisions.
Model-Related Challenges:
- Explainability: Many ML models, intense learning models, operate as "black boxes," making it difficult to understand the reasoning behind their decisions. This lack of transparency can hinder trust and impede effective troubleshooting.
- Model Adversarial Attacks: Malicious actors can exploit vulnerabilities in ML models by manipulating input data or poisoning the training data, causing the model to make incorrect predictions.
Organizational Challenges:
- Skills Gap: A shortage of skilled professionals with expertise in both machine learning and cybersecurity can hinder the successful implementation and maintenance of ML cyber security solutions.
- Integration Complexity: Integrating ML models into existing security infrastructure can be complex and time-consuming, requiring significant effort and expertise.
- Cost: Developing, deploying, and maintaining machine learning and cybersecurity solutions can be expensive, requiring investments in infrastructure, talent, and ongoing maintenance.
- Vendor Lock-in: Relying heavily on proprietary ML cyber security solutions from a single vendor can limit flexibility and increase costs in the long run.
Ethical and Societal Challenges:
- Privacy Concerns: The use of ML in cybersecurity raises concerns about data privacy and individual rights.
- Ethical Considerations: It's crucial to ensure that ML cyber security solutions are used ethically and responsibly, avoiding unintended consequences and minimizing potential biases.
Hence, addressing these challenges is critical for the successful and responsible implementation of machine learning in cybersecurity.
Machine Learning in Cybersecurity: 5 Real-World Success Stories
Seeing is believing. Here are five examples of how leading companies are leveraging machine learning to revolutionize their cybersecurity defenses:

1. Google: Protecting Billions with AI
- Challenge: Google is constantly targeted by cyberattacks that target its users and services, including Gmail, Search, and Android.
- ML Solution: Google employs a sophisticated AI/ML system that analyzes billions of emails, web pages, and mobile apps daily. This system identifies and blocks phishing attempts, malware, and other threats in real-time.
- Impact: Google's AI-powered security systems play a crucial role in protecting billions of users from cyber threats, preventing data breaches, and maintaining a secure digital ecosystem.
2. Microsoft: Securing the Cloud with AI
- Challenge: Securing a vast and dynamic cloud environment like Microsoft Azure requires advanced threat detection and response capabilities.
- ML Solution: Microsoft integrates AI/ML across its security products, including Azure Security Center and Microsoft Defender. These solutions leverage ML cybersecurity to detect and respond to threats such as malware, ransomware, and insider threats.
- Impact: Microsoft's AI-driven security solutions have significantly enhanced the security posture of its cloud platform, protecting businesses and organizations worldwide from cyberattacks.
3. Amazon: Safeguarding E-commerce and Cloud Services
- Challenge: Amazon, with its massive e-commerce platform and cloud computing services (AWS), faces a constant onslaught of cyberattacks targeting its customers and infrastructure.
- ML Solution: Amazon employs machine learning cybersecurity to detect and prevent fraud, identify and block malicious actors, and protect customer data across its diverse business operations.
- Impact: Amazon's AI/ML-powered security measures ensure the security and reliability of its e-commerce platform and AWS cloud security trends services, enabling businesses to operate with confidence in the digital realm.
4. CrowdStrike: Endpoint Protection Redefined
- Challenge: Traditional endpoint security solutions often struggle to keep pace with the rapidly evolving threat landscape.
- ML Solution: CrowdStrike's Falcon platform leverages machine learning cybersecurity to detect and prevent malware, ransomware, and other threats at the endpoint. It analyzes endpoint behavior, identifies anomalies, and provides real-time threat intelligence.
- Impact: CrowdStrike's AI-driven approach has revolutionized endpoint security, enabling organizations to proactively defend against advanced threats and minimize the effects of security incidents.
5. Palo Alto Networks: Next-Generation Firewalls with AI
- Challenge: Traditional firewalls are often limited in their ability to detect and block sophisticated attacks such as zero-day exploits and advanced persistent threats (APTs).
- ML Solution: Palo Alto Networks' next-generation firewalls incorporate machine learning cybersecurity to analyze network traffic, identify malicious activity, and block advanced threats.
- Impact: Palo Alto Networks' AI-powered firewalls provide robust protection against modern cyber threats, enabling organizations to secure their networks and safeguard sensitive data.
These are just a few examples of how leading companies are successfully using machine learning to transform their cybersecurity defenses. As the threat landscape continues to evolve, we can expect to see even more innovative and impactful applications of machine learning in cybersecurity.
Future of Machine Learning in Cybersecurity
The future of machine learning in cyber security is brimming with exciting possibilities. As technology advances, we can anticipate an even more sophisticated and effective role of AI and ML in cyber security solutions. Here are some key trends revolutionizing the future of this dynamic field:
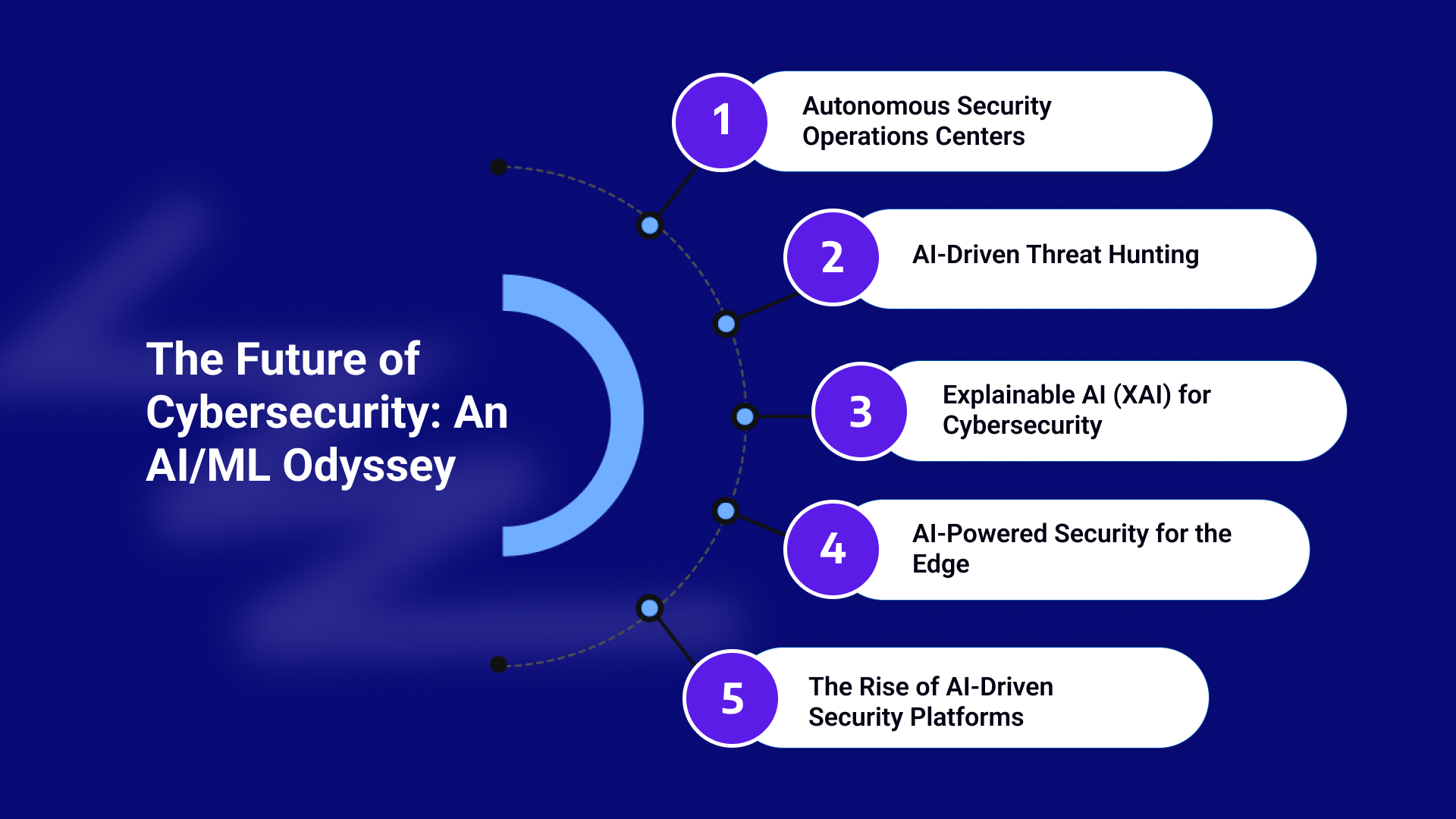
1. Autonomous Security Operations Centers (SOCs):
- Vision: Imagine a SOC where AI/ML automates most routine tasks, allowing security analysts to focus on strategic initiatives and complex investigations.
Machine learning cybersecurity will power autonomous SOCs by automating threat detection, incident response, and security orchestration. AI-powered agents will continuously monitor and analyze threats and autonomously respond to many incidents with minimal human intervention.
2. AI-Driven Threat Hunting:
- Vision: Proactive threat hunting will evolve with AI/ML, enabling security teams to anticipate and proactively hunt for threats they may not even know exist.
ML algorithms will analyze vast datasets, including threat intelligence feeds, network traffic, and user behavior, to identify subtle indicators of compromise (IOCs) and predict potential future attacks. This will enable security teams to be more proactive and prevent attacks before they occur.
3. Explainable AI (XAI) for Cybersecurity:
- Vision: Building trust and ensuring accountability in AI/ML-driven security solutions.
XAI techniques will make AI and ML in cyber security models more transparent and understandable. This will enable security teams to understand the reasoning behind an AI/ML decision, build trust in the technology, and ensure compliance with regulations.
4. AI-Powered Security for the Edge:
- Vision: It will become increasingly critical to secure the growing number of edge devices, such as IoT devices and industrial control systems.
Machine learning in security will play a vital role in securing edge devices by enabling on-device threat detection, anomaly detection, and real-time response.
5. The Rise of AI-Driven Security Platforms:
- Vision: Integrated security platforms that leverage AI/ML across the entire security lifecycle.
We will witness the emergence of integrated security platforms that incorporate AI/ML across all security functions, from threat intelligence and prevention to detection and response. These platforms will provide a unified and comprehensive view of the threat landscape, enabling organizations to respond more effectively to cyberattacks.
The future of AI and machine learning in security holds immense promise. By embracing these trends and addressing the associated challenges, organizations can harness the power of AI and ML to build more robust, resilient, and proactive security defenses.
Choose VLink's Machine Learning Expertise in Cybersecurity
In today's evolving threat landscape, traditional security measures often fail to protect against sophisticated cyberattacks. VLink offers cutting-edge machine learning (ML) consulting services and solutions powered by the latest advancements in ML.
Our dedicated team of highly skilled cybersecurity professionals and data scientists possesses in-depth expertise for ML in cyber security projects, enabling us to develop tailored solutions that address your specific security needs.
With a proven track record of success and a commitment to innovation, VLink delivers robust AI integration solutions for advanced threat detection, intrusion prevention, user behavior analysis, and more. We prioritize customer success, providing ongoing support, maintenance, and training to ensure your security systems remain effective and your team is well-equipped.
Experience the VLink difference by scheduling a free consultation. Discover how our AI and ML in cyber security solutions can enhance your security posture and protect your business from emerging threats.
Wrapping Up!
Machine learning is revolutionizing the field of cybersecurity. By leveraging the power of machine learning in security, businesses can significantly enhance their ability to detect, prevent, and respond to cyber threats. However, machine learning is not a silver bullet. A comprehensive cybersecurity strategy that includes people, processes, and technology is crucial.
By embracing machine learning and adopting a proactive approach to cybersecurity, businesses can better protect themselves in today's increasingly complex threat landscape. For more information on how machine learning in cyber security can help your business protect itself from cyber threats, please contact us.









 Shivisha Patel
Shivisha Patel

















